Some time ago, I exposed an e-shop for blatantly lying about the number of people viewing their products. Their public source code contained a JavaScript function that randomized the number. Since then, the administrators of the e-shop have quietly removed the code from their website.
Well, we are once again exploring the source code of a website, but this time there’s nothing crooked involved. The website that I’ll be showing you today simply exposed hidden promo codes in their public code.
We’ll be looking at a chain of indoor water parks called Great Wolf Lodge today, though I want you to know that it’s actually quite common that websites expose what would be internal information publicly through poor code.
I’ll explain every step along the way, so you can follow along and use the methods I mention in this article to explore the source codes for other websites. And, trust me, you can find all sorts of interesting tidbits in source codes.
Here’s what we’ll do:
-
We will take a look at the source code for Great Wolf, where we will find references to promo codes which we will check out.
-
We will try one of the promo codes on the website and snatch a URL to a web server.
-
Spoiler: in the end, we do find a promo code that works.
Exploring the Source Code
Let’s start by navigating over to our subject: Great Wolf. Right-click just about anywhere on the website and select “View source.” Hit CTRL+F (or CMD+F) to search the code and type “promocode.” We will find two variables in particular that interest me: “dealPromoCodeApiUrl” and “promoCodeList.” The first variable contains a partial URL to a JSON-file (a file with some structured data) that sounds like it would contain promo codes. The second variable is an array (a collection) of promo codes.
If we take the URL found in the aforementioned variable and add “greatwolf.com” to the beginning of it, we’ll end up with this URL: https://www.greatwolf.com/content/experience-fragments/gwl/poconos/experience-fragment/master/_jcr_content/root/plan.json.
At the time of writing, upon visiting that URL, I am greeted with four different promo codes:
 Data found on Great Wolf. Screenshot by the author.
Data found on Great Wolf. Screenshot by the author.
If you visit the URL in your browser, the data might not look as structured as it does for me. Some browsers have a built-in JSON-viewer, but most don’t. However, every major desktop browser has extensions you can install to beautify JSON-files, so you can simply visit your browser’s extension/app store and search for JSON to find one.
Anyway, let’s keep these codes in mind, but let’s also check out that other variable we found before: “promoCodeList.” We already know its contents from looking at in the source, but we can view it more easily in our browser’s console. So let’s open our browser’s developer tools, which you can do in most browsers on a Windows PC by hitting F12. On most computers and browsers, you can also right-click just about anywhere on the website and select something akin to “Inspect element.” After opening our developer tools, we need to select “Console.” Finally, we can type “promoCodeList” and hit enter, and we’ll see five more promo codes:
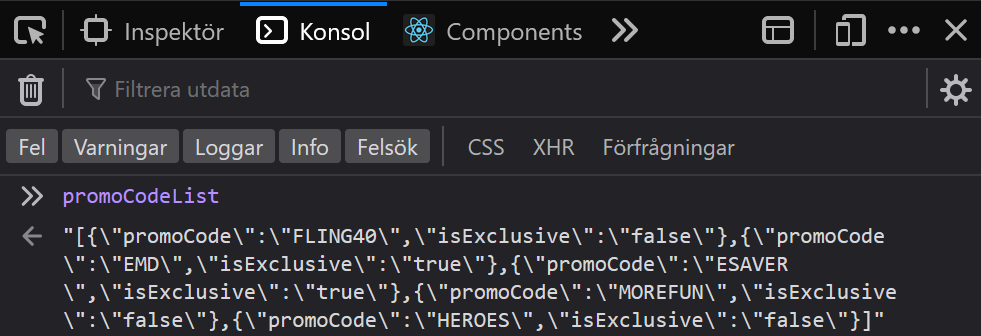 Data found on Great Wolf. Screenshot by the author.
Data found on Great Wolf. Screenshot by the author.
Let’s try one of these. On Great Wolf’s home page, there’s an option to search for available dates close to the top of the screen. I’ll search for some dates, select one guest, and enter a promo code that I discovered previously: PROMO20.
 Screenshot from Great Wolf by the author.
Screenshot from Great Wolf by the author.
After the search is complete, I am greeted with a piece of text saying: “Unfortunately that is not a valid offer code. Please re-enter or view our other offers.”
Talking To the Web Server
I’m always curious to see how data is sent back and forth between the website and the web server, so let’s head over to our developer tools’ network tab. Select “XHR” to see what data goes between the webpage and the web server. If the tab is empty, refresh the webpage. The network tab is now filled with API calls. If you don’t know what acronyms like XHR and API mean, don’t worry; they basically mean that the website is talking to the server.
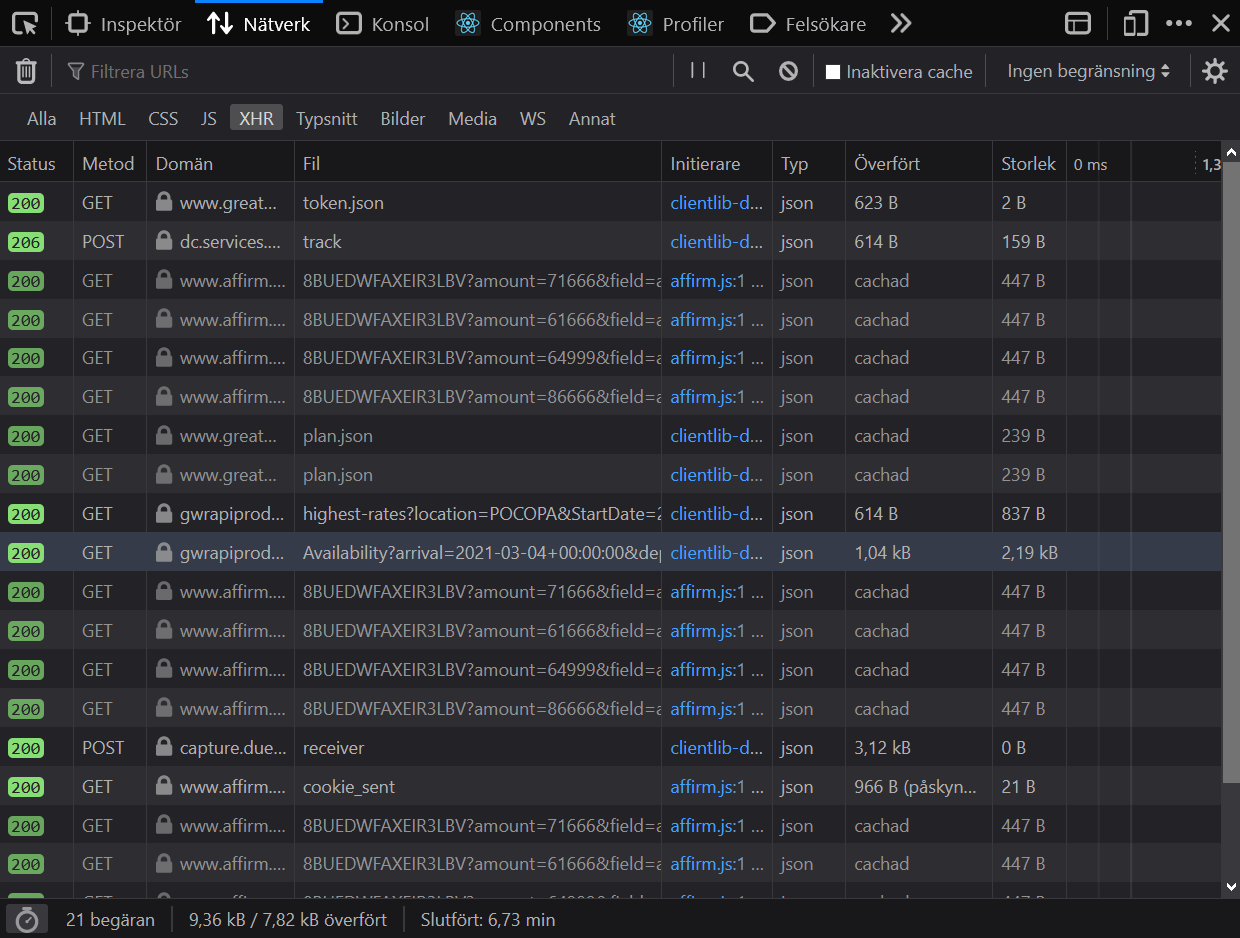 Network calls made on Great Wolf when searching for a suite. Screenshot by the author.
Network calls made on Great Wolf when searching for a suite. Screenshot by the author.
Most of these don’t sound very interesting, but the highlighted row catches my attention. It says “availability” and looks like it sends interesting data. If I click on it, my browser will expose a URL that the website uses to ask the server for available suites.
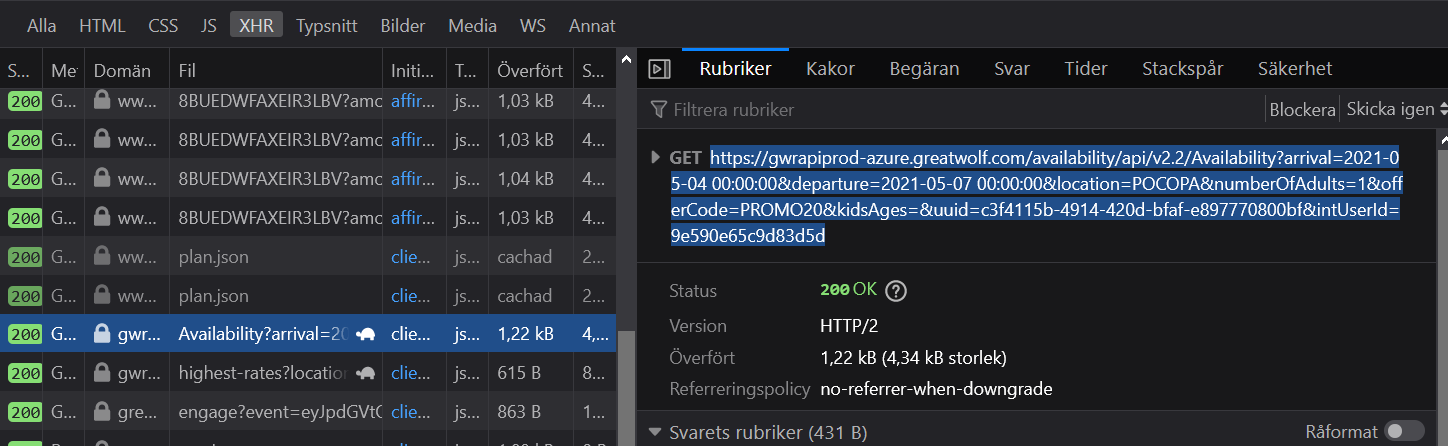 Network calls made on Great Wolf when searching for a suite. Screenshot by the author.
Network calls made on Great Wolf when searching for a suite. Screenshot by the author.
If you click on the URL exposed in this network tab at the time of writing, you’ll end up on another page full of data. The results on this page contain suites that are available for our selected dates. Conveniently, at the top of the data is information regarding the promo code. There’s an error code that says the offer is invalid (which we already knew).
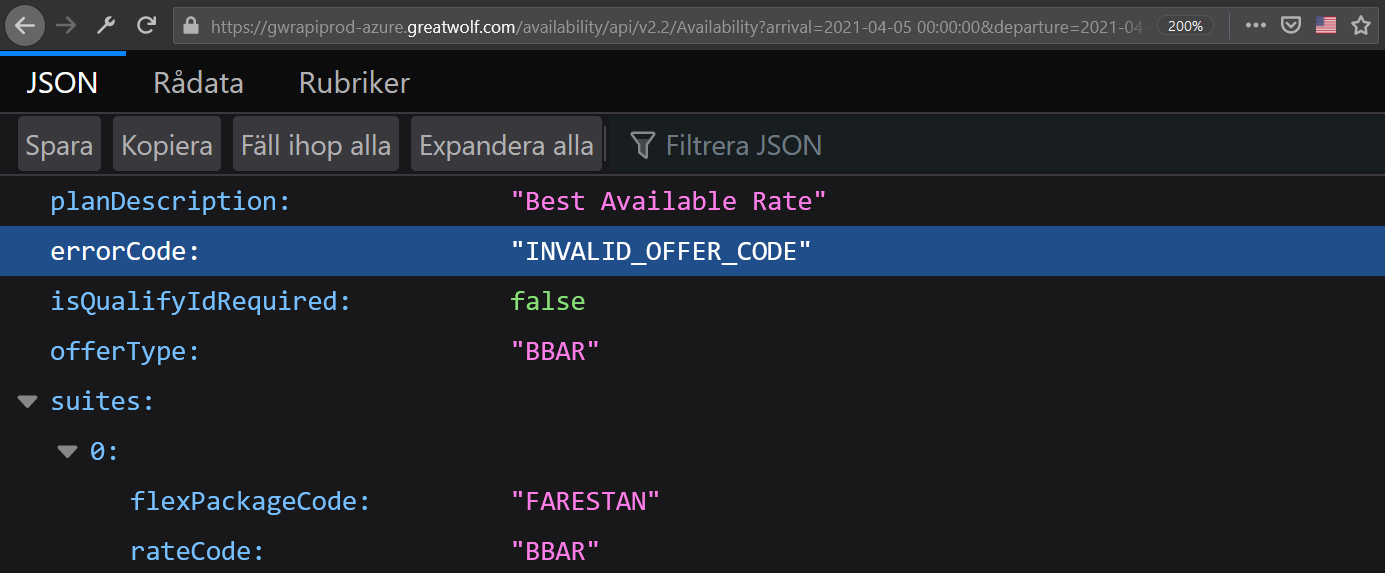 Data found on Great Wolf. Screenshot by the author.
Data found on Great Wolf. Screenshot by the author.
Sadly, the data isn’t too interesting, but this URL makes it easier for me to try other promo codes. See, if you look at the URL, you’ll find a bit that says “offerCode=PROMO20.” I can enter a different promo code here and reload the URL to try it out. Before long, I land on a hit. One of the promo codes I found earlier works: “FLING40.” At the time of writing, if you click here, you will receive this response:
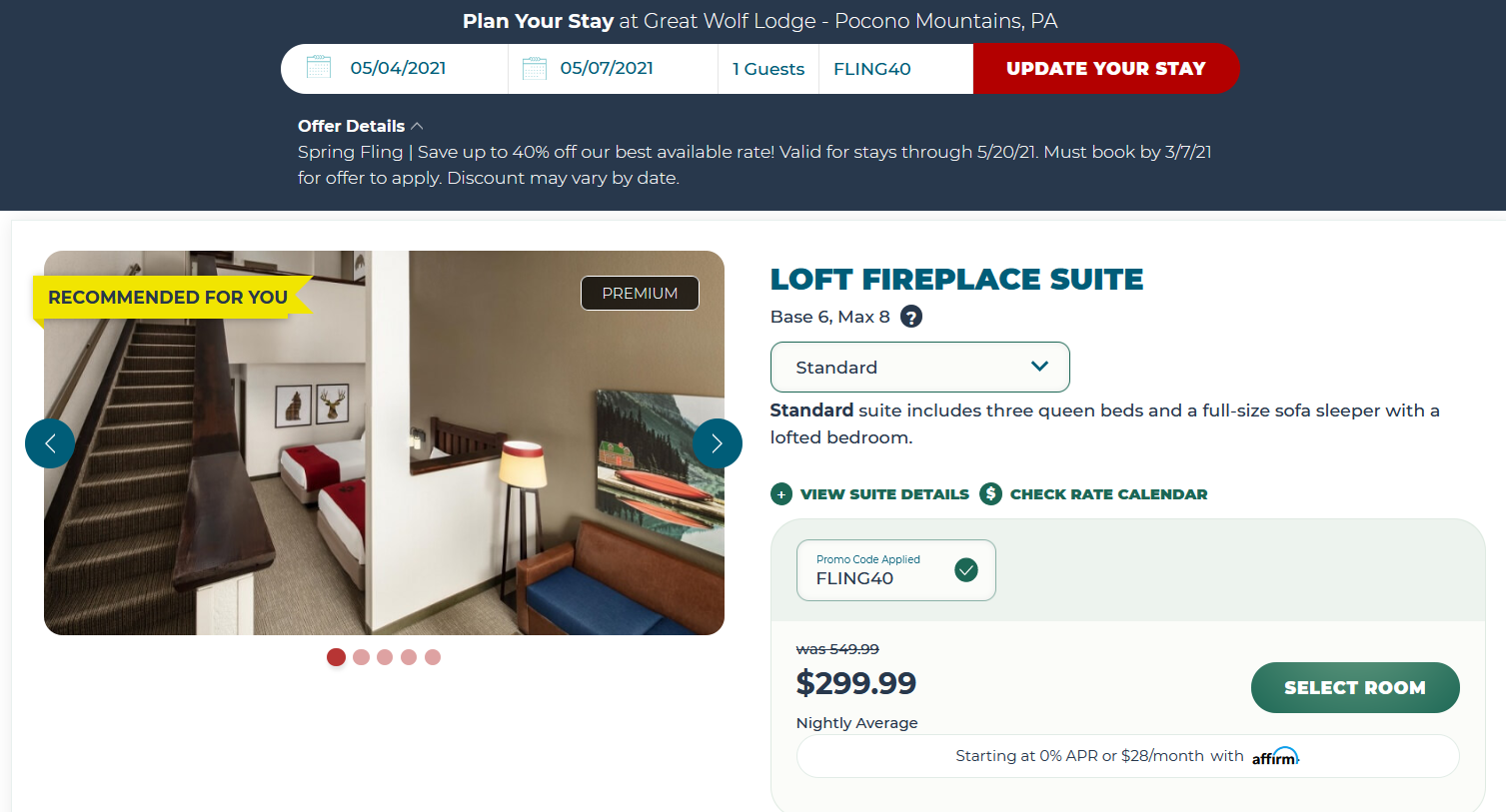
Mission successful.
I should also mention that some of the promo codes we found earlier are listed in plain sight over at Great Wolf’s “deals”-page. However, the code FLING40, which we ended up using, is not on there.
In summary
We went through a number of very simple techniques to discover promo codes for a booking website. We looked at the source code and found some interesting JavaScript variables. We checked them out and found a number of hidden promo codes. We also found a URL to talk to Great Wolf’s web server to test the codes more quickly. In the end, we found a hidden promo code that worked.
You might be wondering why the promo codes were just lying there in some random variables in the public source code to begin with. There could be plenty of reasons, but from my own experience working as a developer, I’d say it’s usually because of management issues. Tight deadlines, lack of a rigorous testing phase, late additions to the scope, or a poorly-written requirement sheet could be reasons for leaving data exposed like this.
Besides, since the data is benign, there may also have been no reason to remove it. It’s an innocent mistake that’s more common than one might imagine. Of course, I do have to mention that leaving the code in could also be done intentionally as a genius trick to gain exposure or drive sales. But I do find that very hard to believe.
In any case, I hope you learned something new, and happy hunting for goodies in other source codes.
Thanks for reading! If you enjoyed this article, you will probably enjoy these two pieces of text as well:
