The simple HTTP server is a feature from python that allows us to create an HTTP server in a simple way. In another way, usually, hackers or penetration testers use this method to transfer files between the attacker machine (Kali Linux) to the victim machine. Because of the assumption that firewalls usually allow access from inbound port 80 or HTTP.
The cons of this method are, that all the communication is unencrypted because just with HTTP. While the attacker transferred the malware into the victim machine, so, the Blue Team / Threat Hunter found our methodology to attack easily.
There is one answer to making the Blue Team hard to do forensics, it encrypts the communication while transferring malware.
But, how?
Let's get started
Actually, I got this script from Red Team Field Manual (RTFM), I attach the link if you are interested in this book.
Before going to the script, firstly prepare for the SSL certificate (private key and public certificate). If you are new in this field, just looking my previous article about SSL certificates.
or you can do this command in your Linux terminal
openssl req -new -x509 -keyout cert.pem -out cert.pem -days 365 -nodes
Let's say you have a cert file and a private key or you run the command above and have a single cert.pem file.
In this example, I use step 2 for generating an SSL certificate. So, now I just have cert.pem.
If you have a private key and cert file. Just read this information below for a little enhancement in your code.
Information from https://docs.python.org/3/library/ssl.html#ssl-contexts
The next step is to create a file called https-simple-server.py or anything you want to be the name of the file.
Put the code below into that file:
# Date : 17 - 08 - 2022
# Ref: RTFM v2
Python3 simple-https-server.py
import http.server, ssl, socketserver
context = ssl.SSLContext(ssl.PROTOCOL_TLS_SERVER)
context.load_cert_chain("cert.pem") # PUT YOUR cert.pem HERE
server_address = ("192.168.43.210", 4443) # CHANGE THIS IP & PORT
handler = http.server.SimpleHTTPRequestHandler
with socketserver.TCPServer(server_address, handler) as httpd:
httpd.socket = context.wrap_socket(httpd.socket, server_side=True)
httpd.serve_forever()
Run this program with this command:
Python3 simple-https-server.py
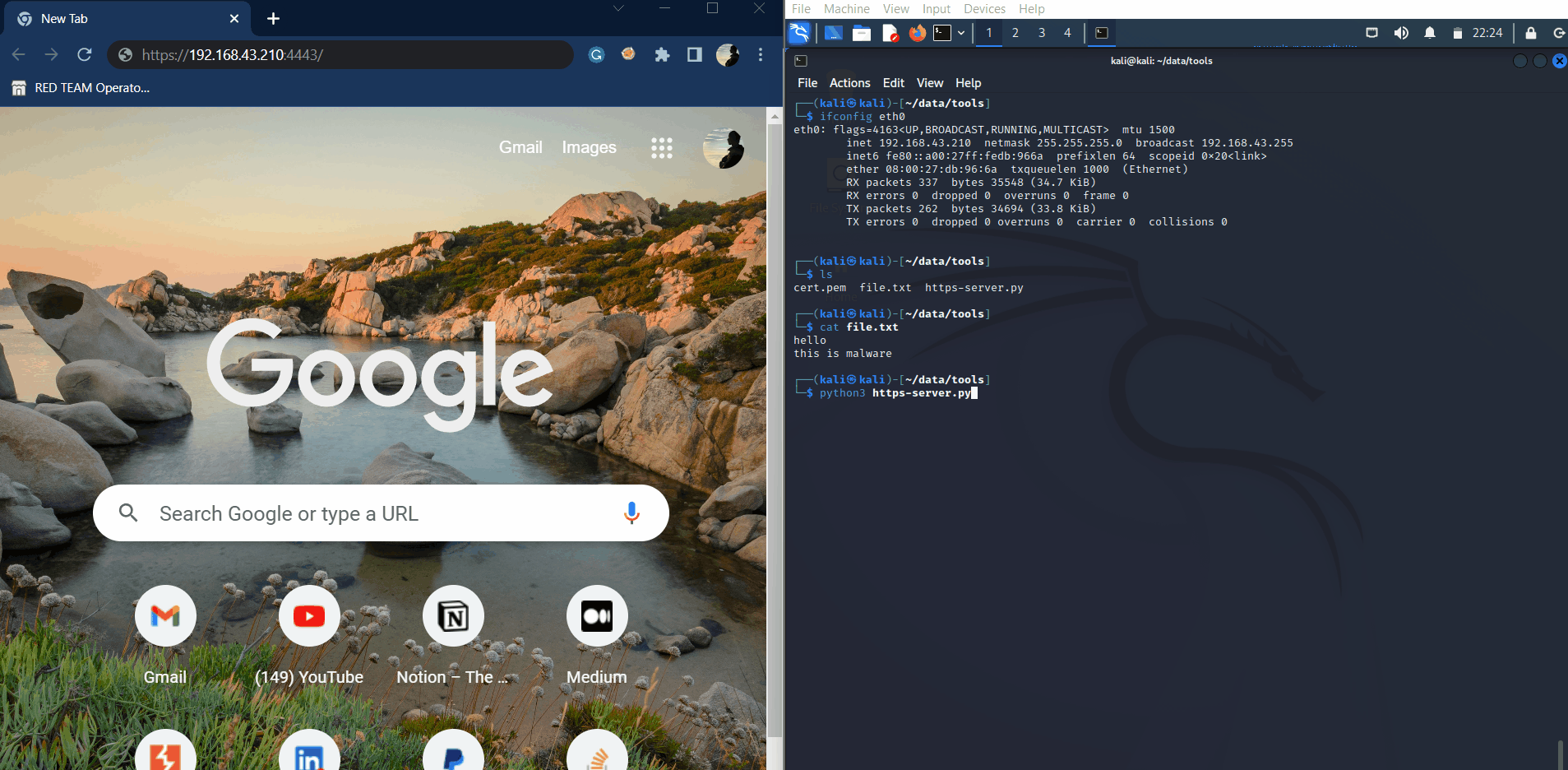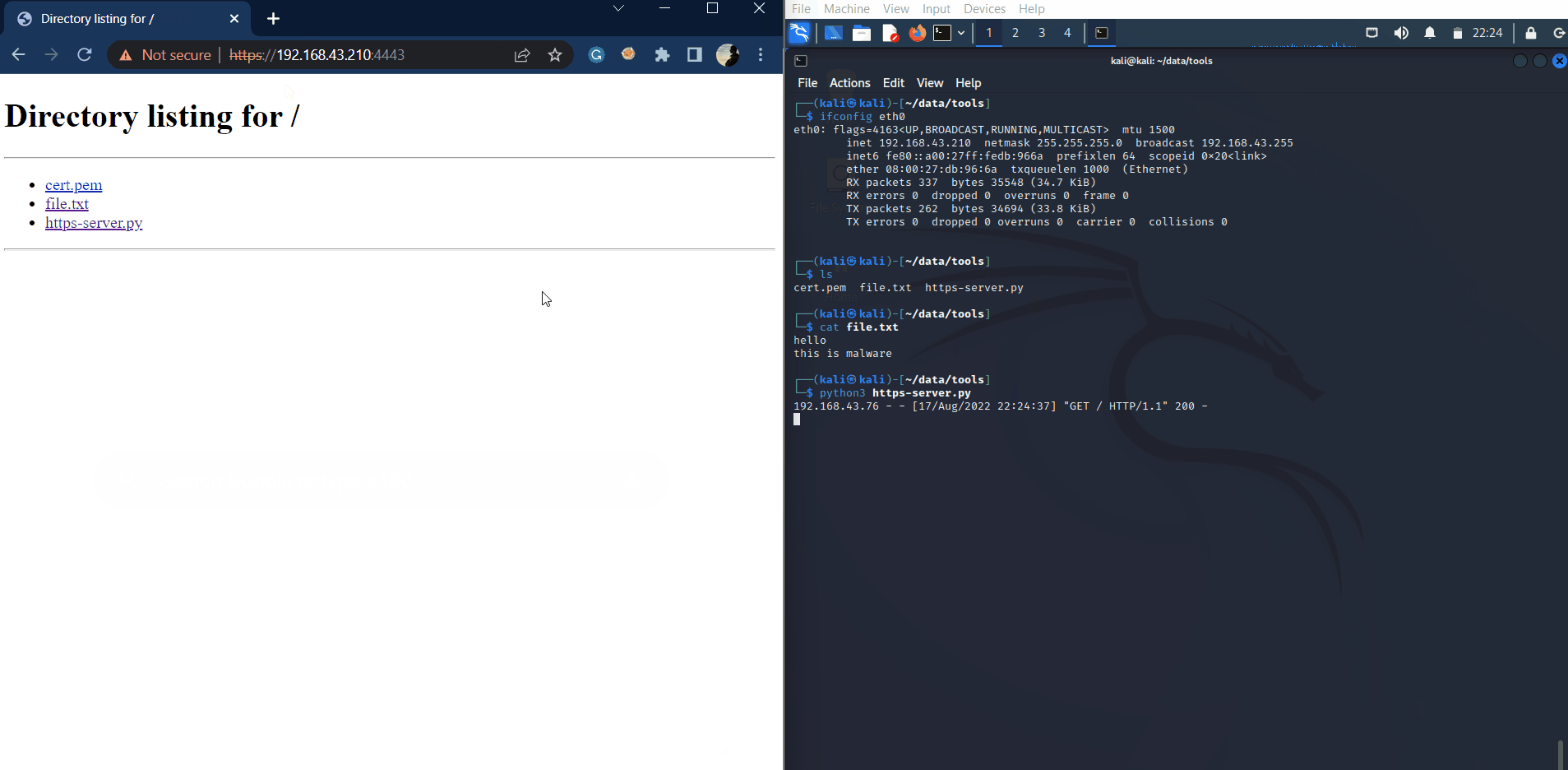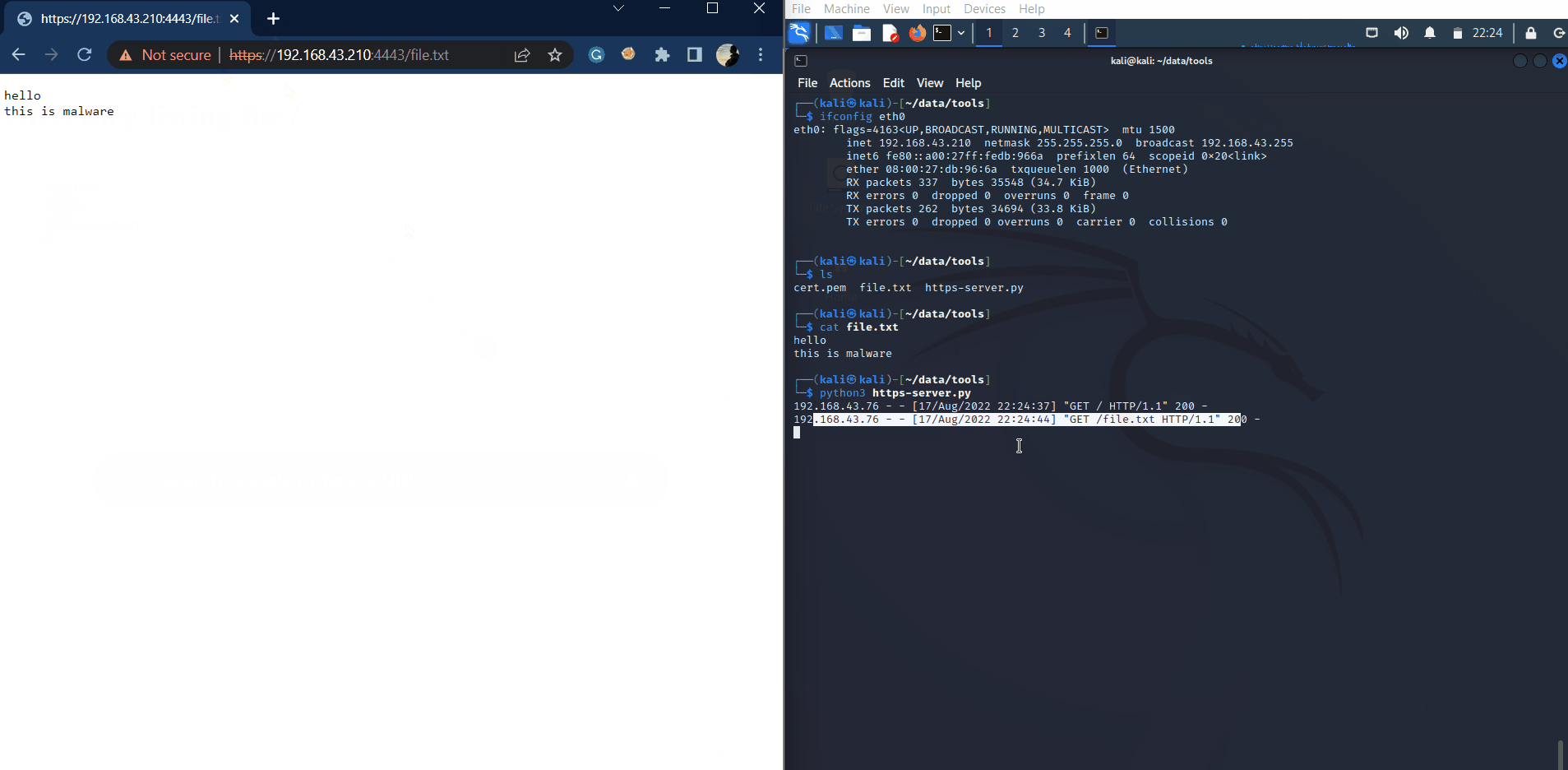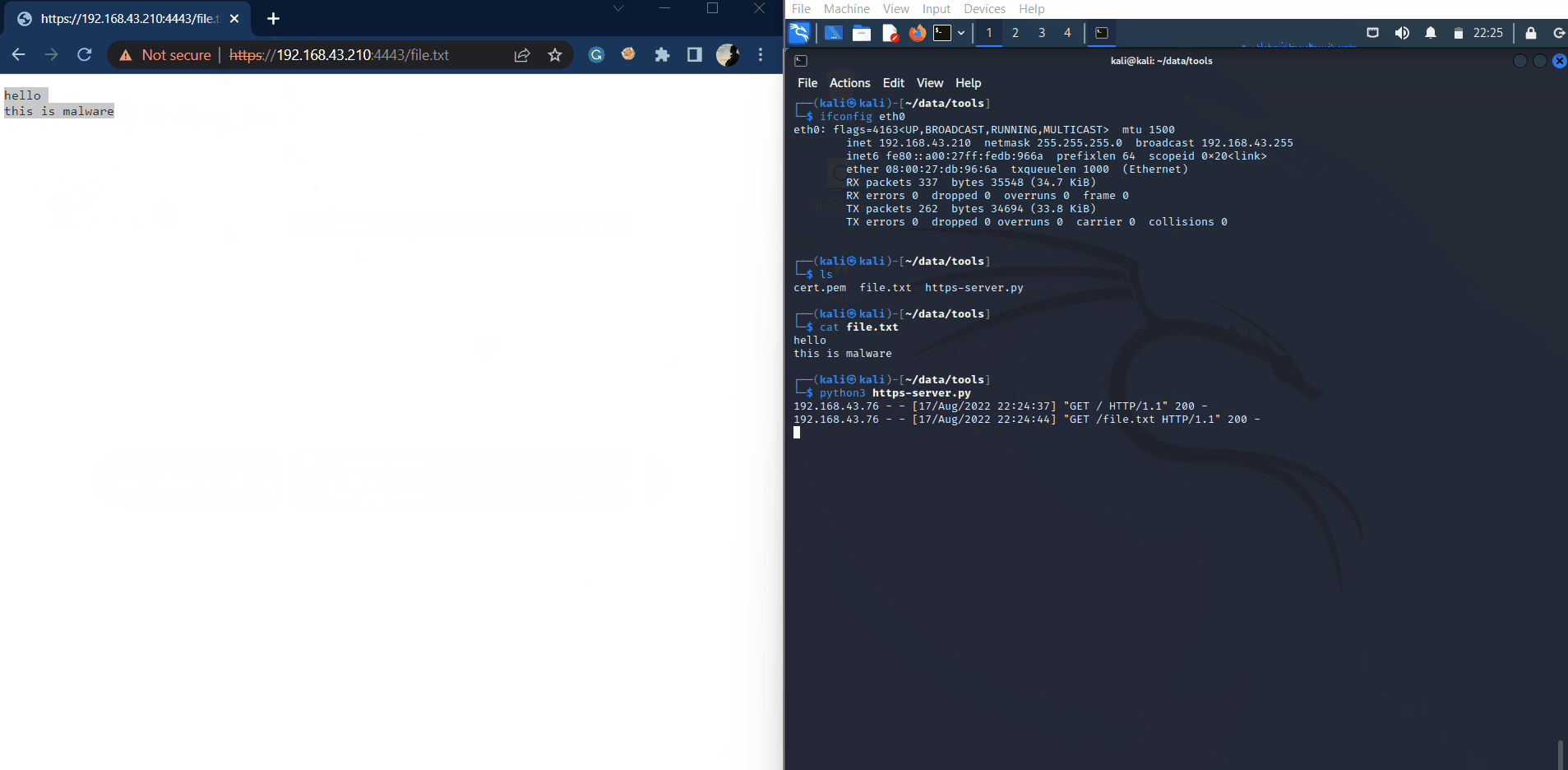
Then access the server with the browser of the other machine:
https://<IP>:<port>
Finally, enjoy your encrypted transfer file with this simple HTTP server + SSL certificate.
Prove of Concept with Wireshark
Unencrypted
If you use HTTP in transferring files, it's will seem like this:
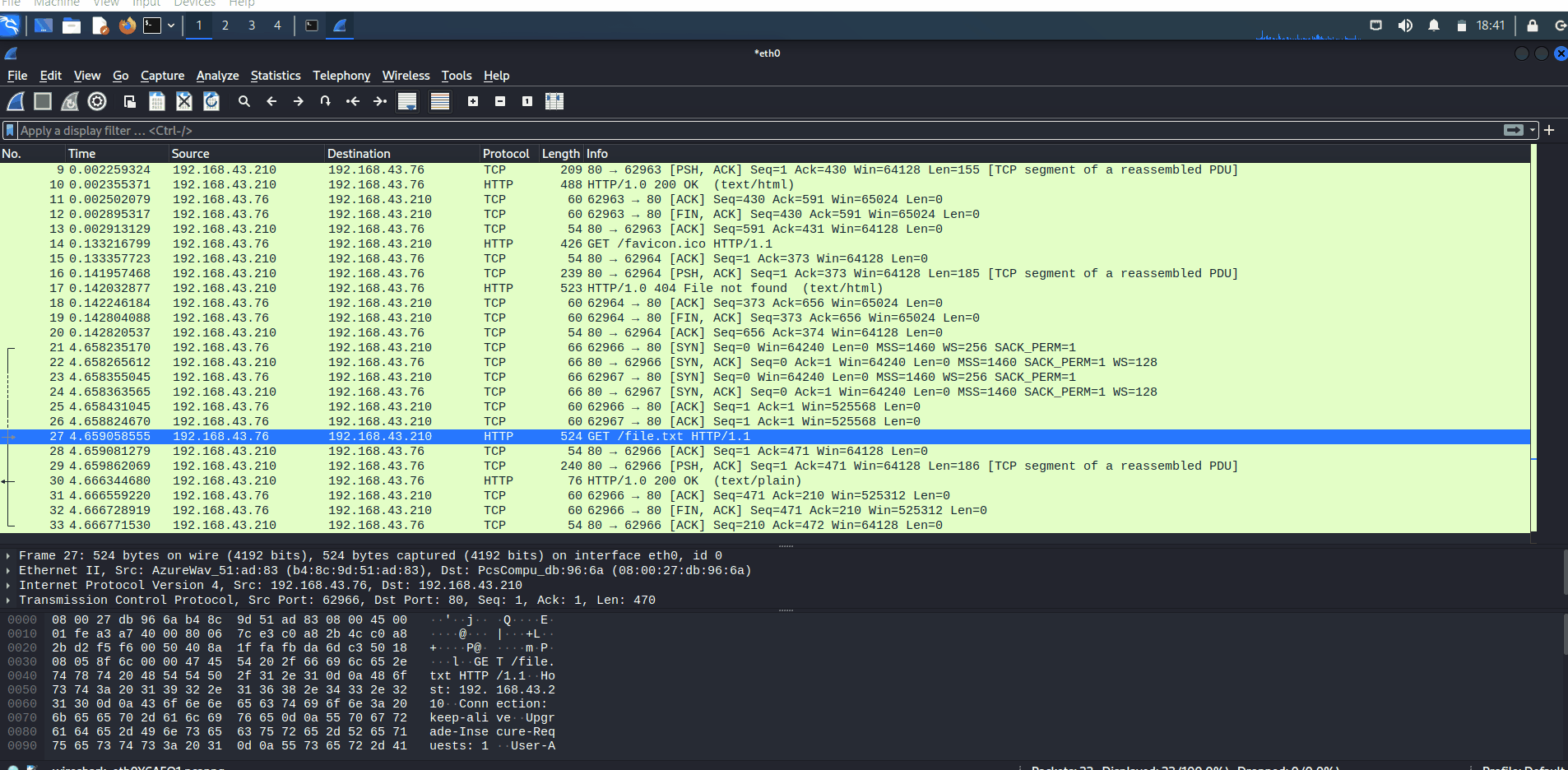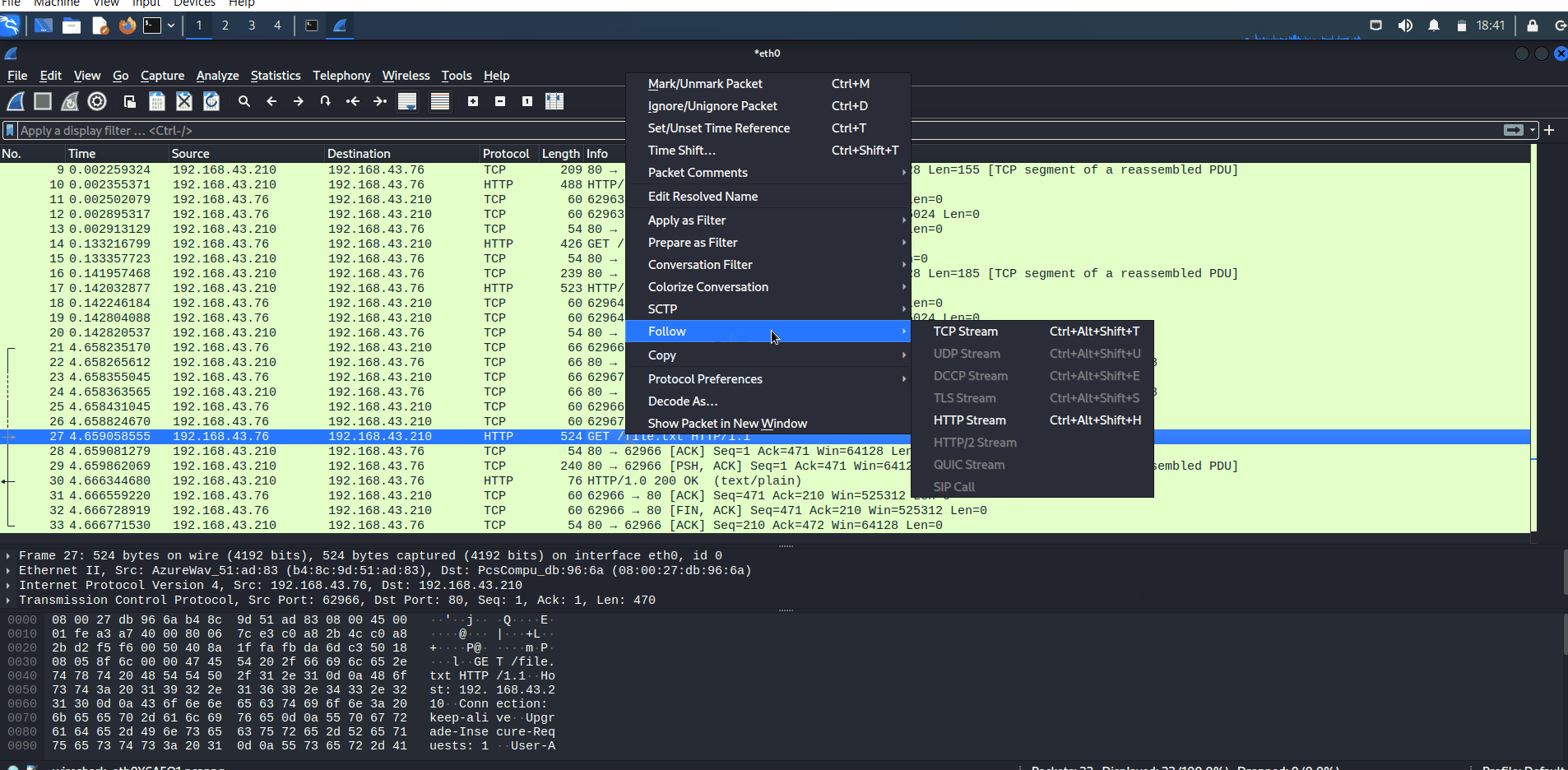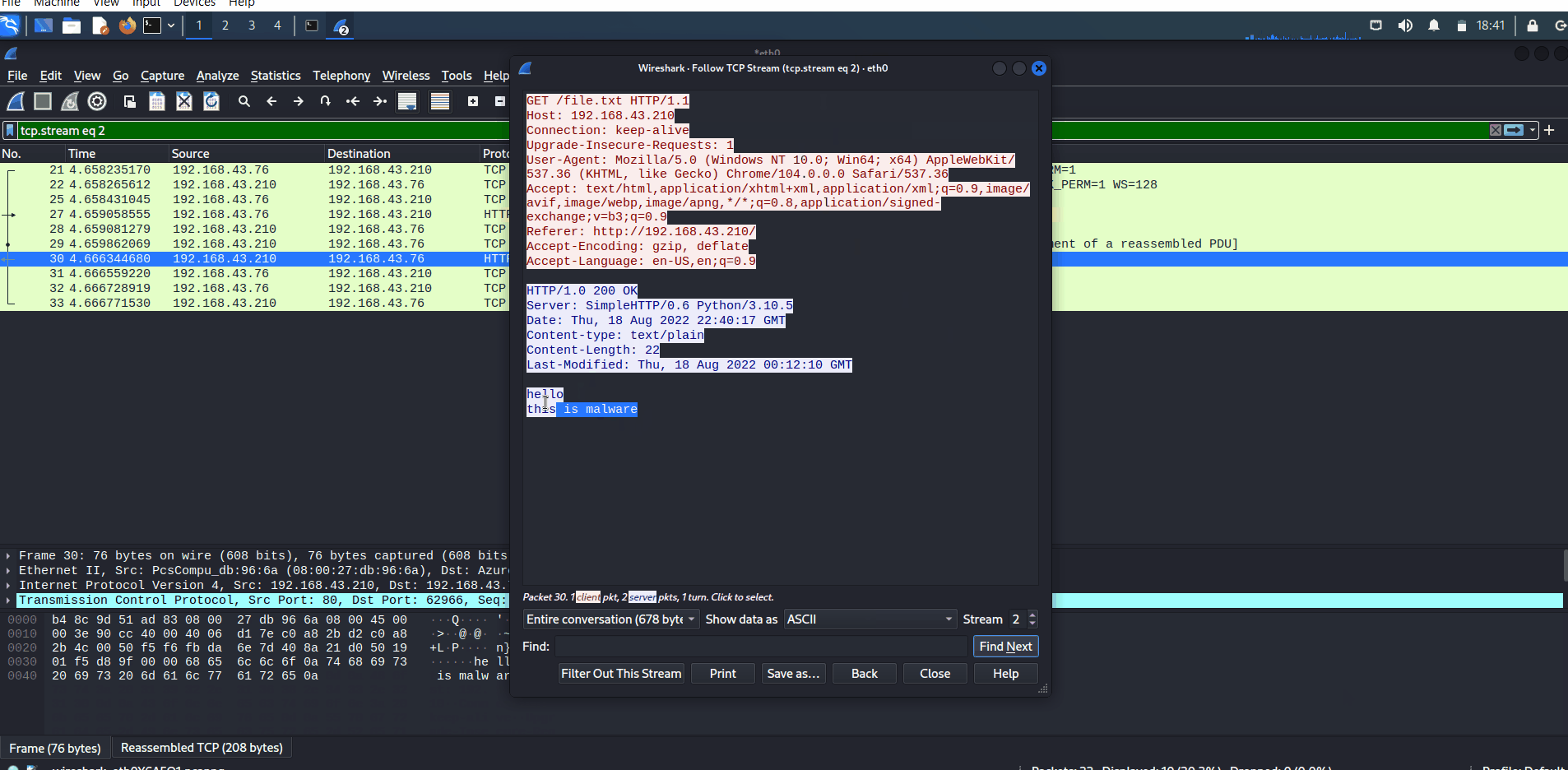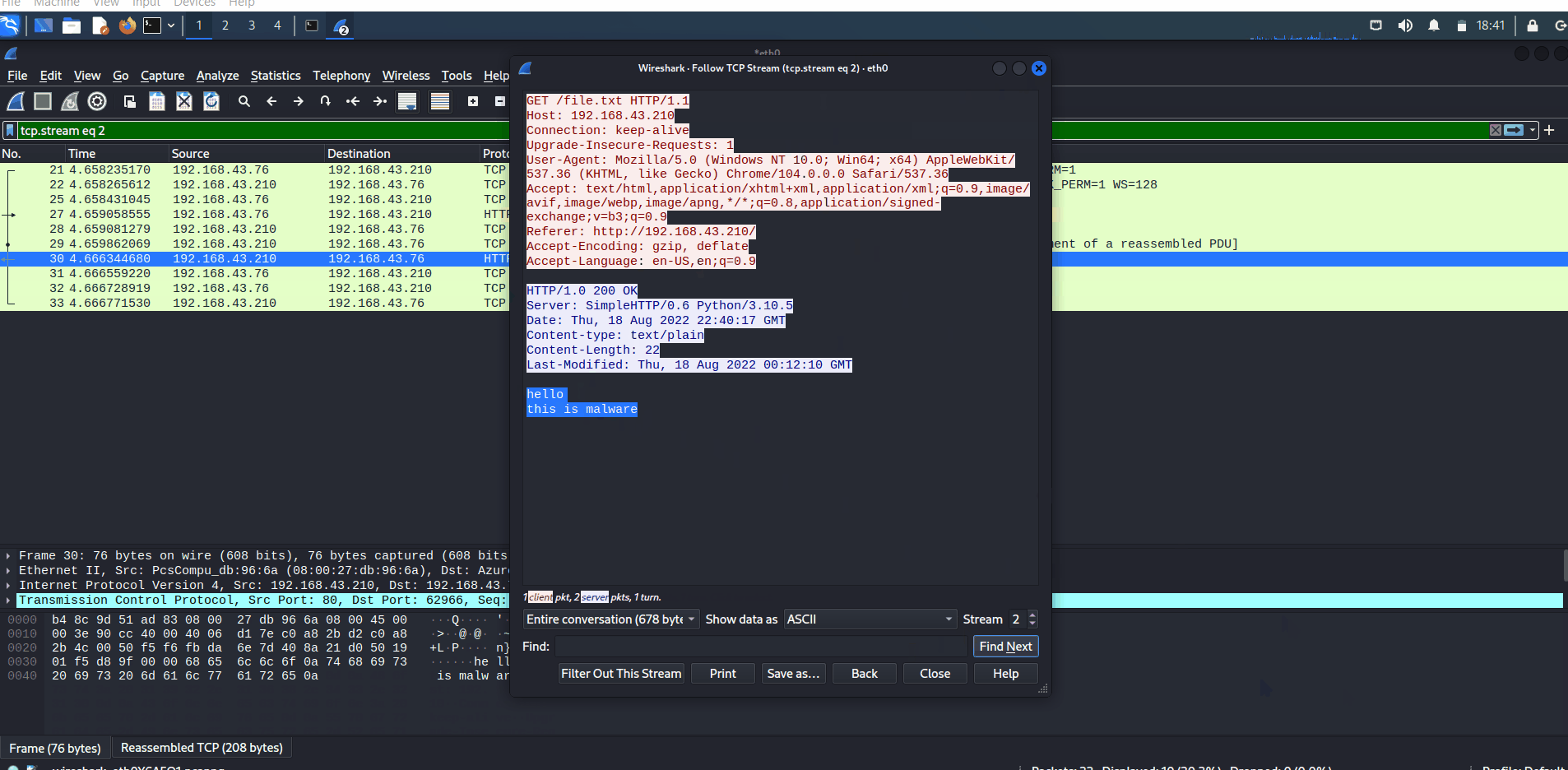 Wireshark captures HTTP traffic
Wireshark captures HTTP traffic
Encrypted
On the other side, when you use HTTPS to transfer files, all of the information will be encrypted.
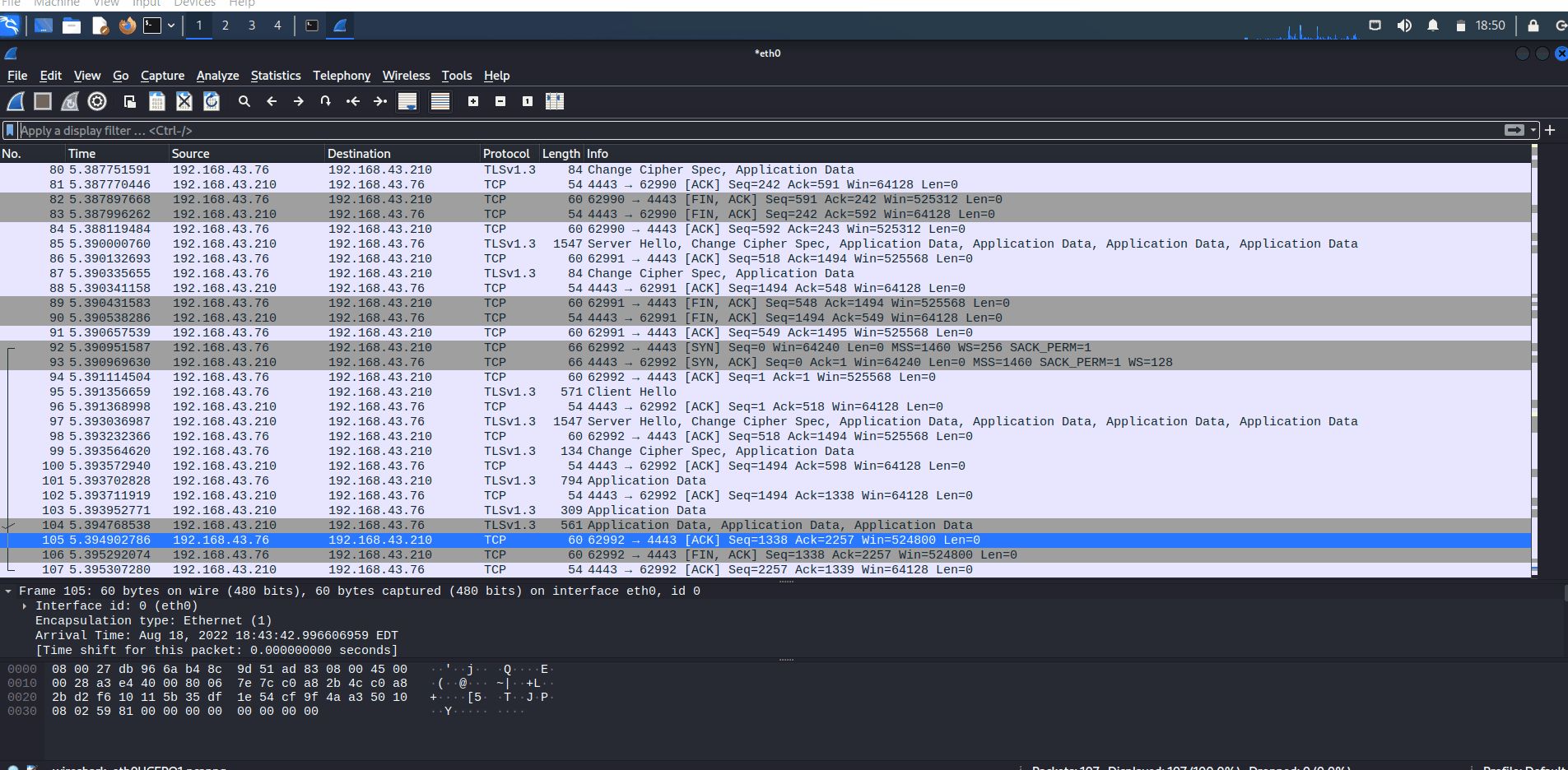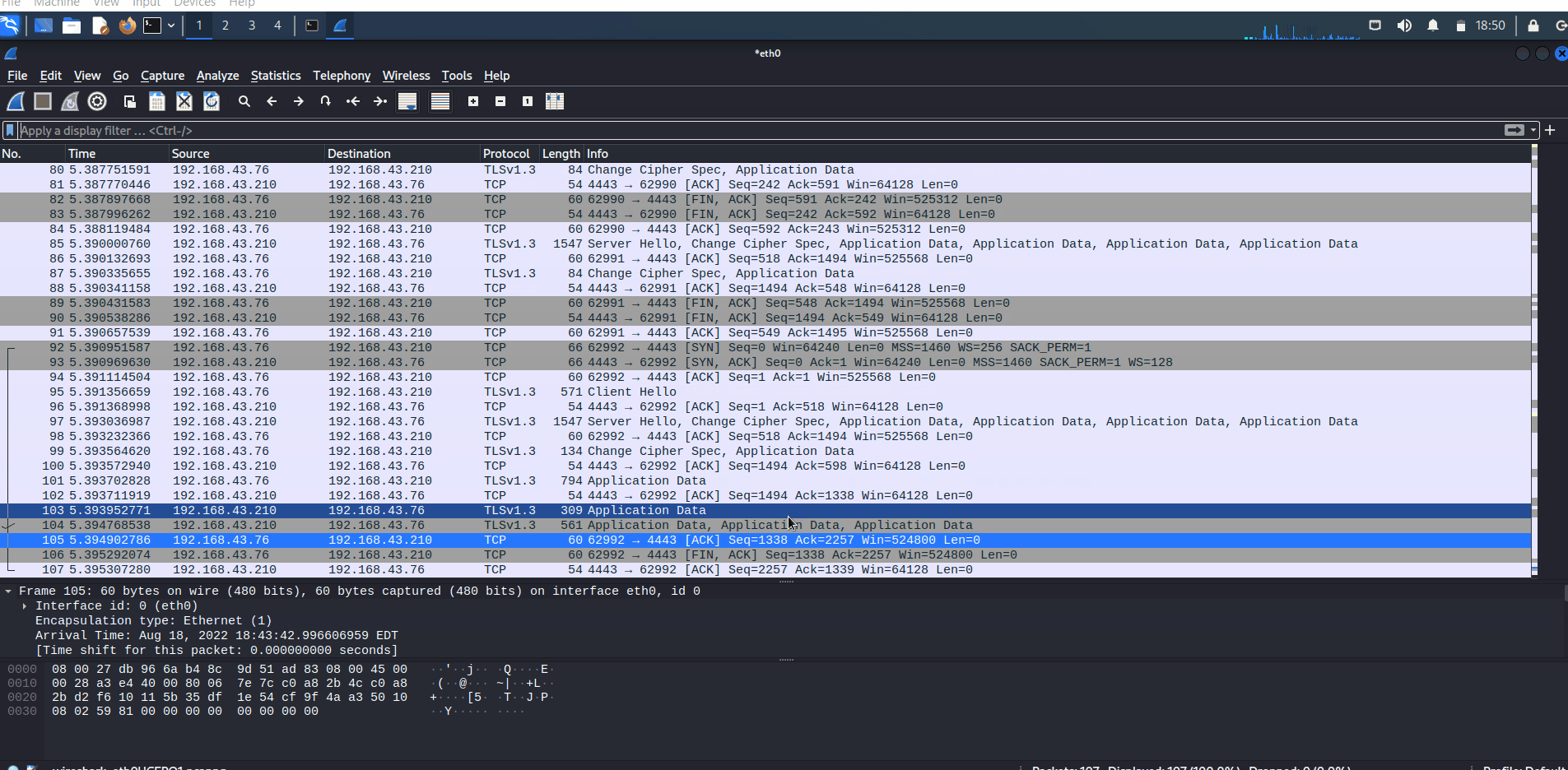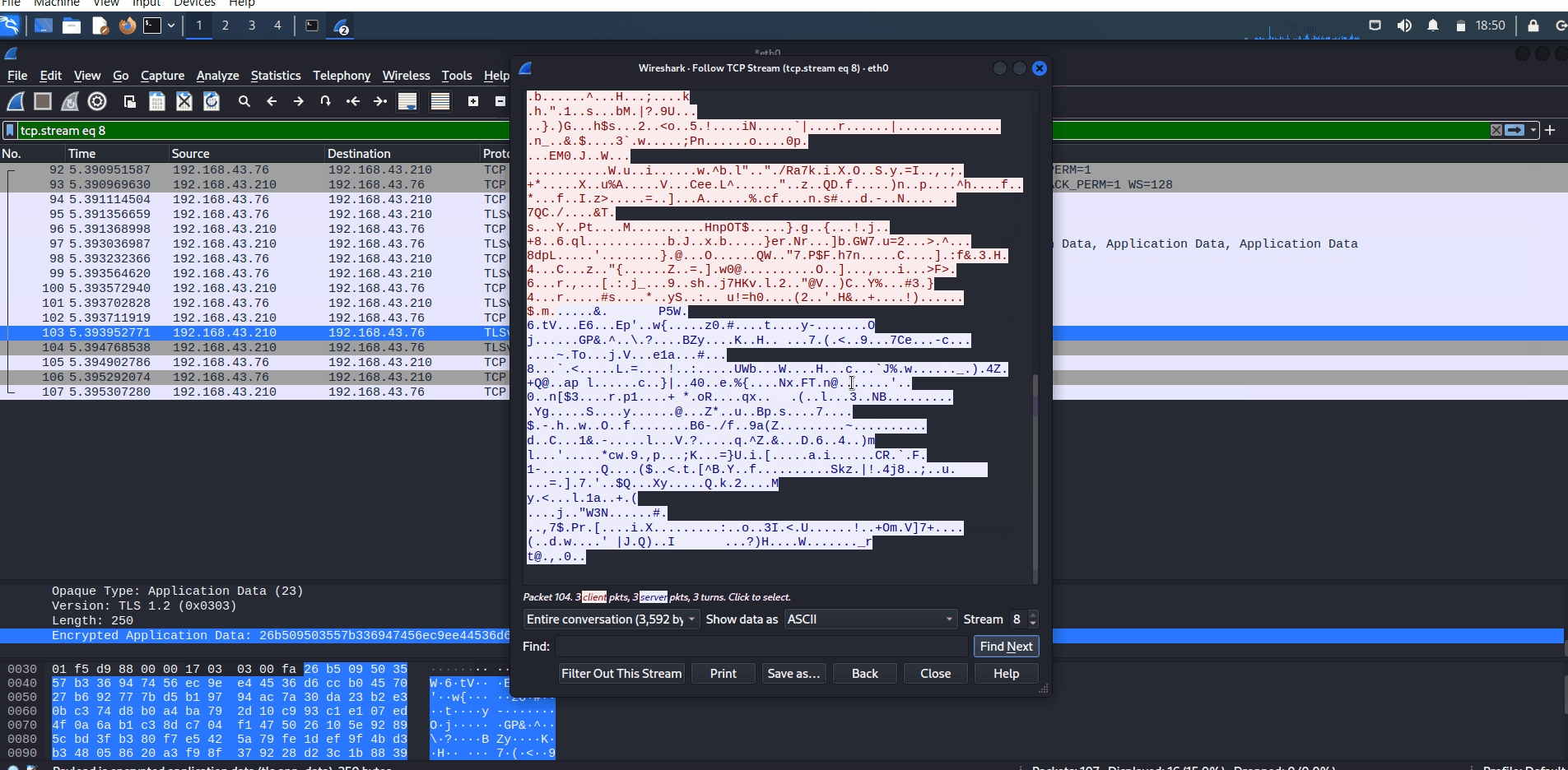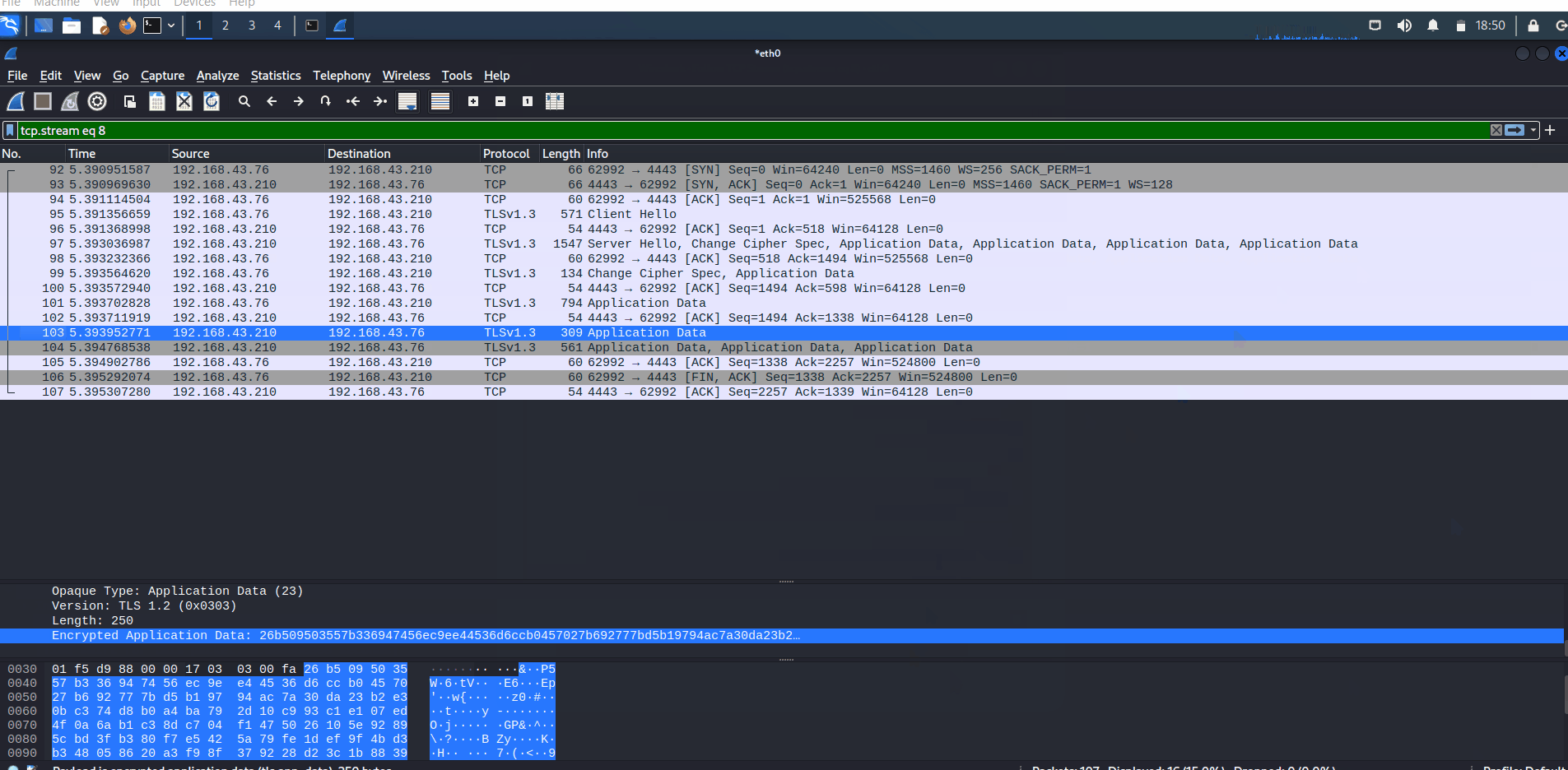 Wireshark captures HTTPS traffic
Wireshark captures HTTPS traffic
Conclusion
Keep your way as simple as you know, so you are not afraid of tools and processes. This python feature makes me feel easy to set up the transferring file in the daily job or night job as a CTF player.
Reference: RTFM: Red Team Field Manual v2
Comments
Loading comments…