Contributors:
- Ajith Joseph, Manager, Deloitte;
- Noel Arzadon, Specialist Master, Deloitte;
Introduction
Ensuring seamless connectivity between on-premises networks and AWS resources is paramount in today’s hybrid cloud environments. AWS Control Tower provides a centralized hub for managing multi-account AWS environments, while the Account Factory Terraform (AFT) feature offers a way to further tailor and automate deployments. In this blog, we’ll dive into the world of customization within AWS Control Tower’s hybrid environment, shining a spotlight on a practical example: setting up DNS outbound resolvers. This example demonstrates how integrating Terraform within AWS Control Tower can streamline networking setups and strengthen connectivity between on-premises and cloud environments in a natural, intuitive way.
Why Customization Matters: While AWS Control Tower provides foundational guardrails for AWS account management, customizations such as outbound DNS resolvers are typically organization-specific. Each organization operates within a unique context, with distinct networking requirements, security protocols, and operational workflows. By embracing customization, businesses can tailor their infrastructure setups to align perfectly with their specific needs and existing architectures. This not only ensures compatibility with hybrid network infrastructure but also allows organizations to uphold stringent security standards, adhere to compliance regulations, and optimize performance. Customization empowers organizations to maintain control over their infrastructure configurations, adapt swiftly to evolving business demands, and foster a seamless integration between on-premises and cloud environments.
The Role of Terraform in AWS Control Tower: Terraform’s infrastructure as code approach offers a powerful solution for automating the deployment of complex network, security and infrastructure configurations. By integrating Terraform with AWS Control Tower’s Account Factory Terraform (AFT) feature, organizations can define and deploy custom configurations across multiple AWS accounts consistently. This integration streamlines provisioning processes, enhances scalability, and promotes infrastructure agility.
Use Case
Hybrid DNS Outbound Resolvers: Consider an organization with a hybrid cloud environment where AWS resources need to communicate with on-premises servers. Sometimes there is a need to selectively apply outbound DNS resolvers within each AWS account provisioned by AWS Control Tower facilitates DNS resolution to on-premises networks securely, providing flexibility in scenarios where a centralized network account may not be suitable. This ensures reliable connectivity and enables applications hosted in AWS to seamlessly interact with on-premises services.
Outbound revolvers are used to address the below needs:
- Resolve DNS queries for on-premises resources: If the organizations workloads leverage both VPCs and on-premises resources, outbound resolvers enable DNS resolution between your VPC and on-premises network. This facilitates communication and data flow between your AWS and on-premises environments, establishing a hybrid cloud setup.
- Route DNS queries to specific DNS servers: Outbound resolvers allows to configure rules that direct DNS queries for specific domain names to designated DNS servers, either on-premises or within another VPC. This provides granular control over DNS resolution for certain domains, potentially improving performance or adhering to specific compliance requirements.
- Forward DNS queries from VPCs: Outbound resolvers can be used to forward all DNS queries originating from VPCs to a designated DNS server, such as on-premises DNS server. This can be useful if the organization want to centralize all DNS resolution within organization’s hybrid ecosystem.
Code snippets
To selectively apply the customization for the outbound resolver only to accounts that need to communicate with on-premises resources, we recommend introducing a condition in AWS Control Tower Account Factory Terraform (AFT) configuration. This condition can be based on on factors such as account tags, organizational policies, or specific requirements that determine whether DNS resolution to on-premises resources is required for a particular AWS account.
In our example to keep it simple we are using the “account_customiztions_name” parameter within the account request for specific account type terraform template. Using this parameter ensures that customizations apply at account level to each account provisioned through the AFT pipelines. It will also give us granular control on which accounts/organizational units(OU) that these customizations can be applied to.
Below is the folder structure used for our example. The hybrid DNS terraform template is placed within the workload-customizations folder in the aft-account-customizations repository.
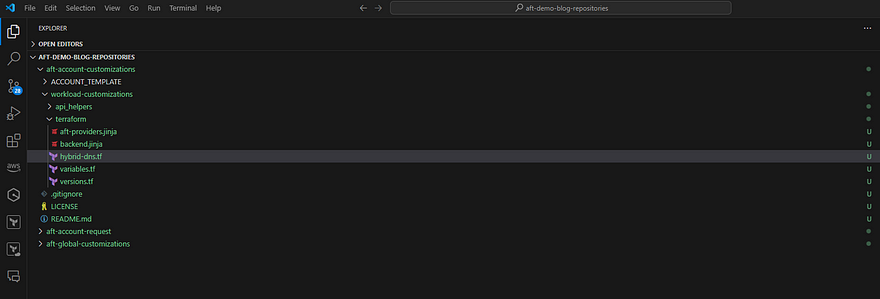
Global customizations can also be applied if the customization use case needs to be applied to all the accounts provisioned via AFT pipelines. Ex: Adding SSM roles to each account, creating S3 buckets for CloudFormation templates etc.
Pre-requisites:
- Familiarity with AWS Control Tower and its Account Factory Terraform module.
- Proficiency with Terraform for infrastructure as code (IaC) deployment and management.
- Basic knowledge of domain names resolutions.
Defining variables
Define the variables to hold the list of domain names for outbound resolution and the IP address of the on-premises DNS server.
# Variable list for domains and on-premises DNS server
variable "dns_domains" {
type = map(string)
description = "List of domains associated with IP address"
default = {
"test-example.gov" = "1.2.3.4"
"test.com" = "5.6.7.8"
}
}
variable "dns_ips" {
type = list(string)
description = "List of DNS server IP addresses (dummy for illustration)"
default = [
"10.0.0.1",# Dummy DNS ips
"10.0.1.1"
]
}
Resolver Rules and Endpoint template snippets.
The outbound resolver rules and endpoint as necessary for each workload account is defined in workload-customizations folder within the account customizations repository.
# Resource creation - Outbound resolver
resource "aws_route53_resolver_endpoint" "outbound_resolver" {
name = "outbound-resolver"
direction = "OUTBOUND"
security_group_ids = [aws_security_group.resolver_sg.id]# Replace the details as needed.
dynamic "ip_address" {
for_each = var.dns_ips
content {
subnet_id = aws_subnet.public_subnet[0].id # Assuming these vaiables for simplicity
ip = ip_address.value # Use variable for dynamic IP assignment
}
}
tags = {
Name = "DNS Resolver"
}
}
# Resource creation - Resolver rule
resource "aws_route53_resolver_rule" "resolver_rule" {
for_each = var.dns_domains
name = "resolver-rule-${each.key}"
domain_name = each.value
rule_type = "FORWARD"
resolver_endpoint_id = aws_route53_resolver_endpoint.outbound_resolver.id
target_ip {
ip = var.dns_ips[each.key] # Use variable for dynamic IP assignment
}
}
Using parameter reference while creating account
The parameter “account_customization_name” in the primary account request Terraform template serves as a reference for the account-specific customizations required for the particular type of accounts being provisioned. In our context, we direct it towards the “workload-customizations” directory within “aft-account-customizations” to ensure the execution of the “hybrid-dns.tf” file in each account provisioned through the AFT pipelines, thus facilitating the creation of outbound resolvers.
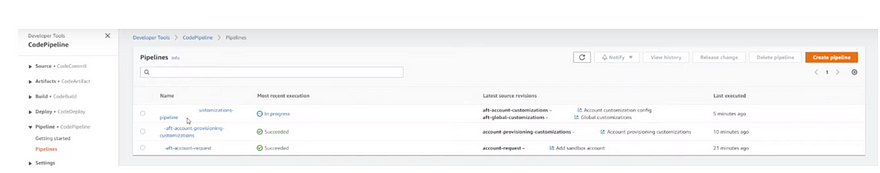
Initiating the creation of a workload account will activate the corresponding aft-account-customizations code pipeline, as depicted below. This process ensures the establishment of necessary outbound resolvers within the associated account.
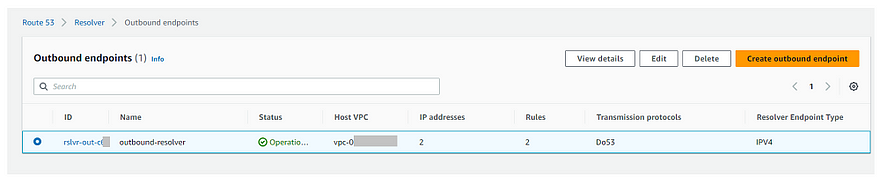
Benefits and Considerations: Customizing outbound DNS resolvers with Terraform in AWS Control Tower offers several advantages. It provides flexibility to adapt DNS configurations to organizational needs, promotes consistency across AWS accounts, and enhances security by aligning with existing network policies. However, organizations must carefully consider IAM permissions, security, and maintenance requirements to ensure the reliable operation of hybrid DNS resolution.
Conclusion
Customizing AWS Control Tower using Terraform offers organizations the flexibility to tailor their cloud infrastructure to specific needs, beyond just DNS resolution. Deploying outbound DNS resolvers is just one example of the myriad customizations possible.
For instance, organizations can leverage Terraform to implement custom security policies, automate resource provisioning workflows, or enforce compliance standards across AWS accounts. By harnessing the power of Terraform and AWS Control Tower, organizations can streamline operations, enhance security, and adapt to evolving business requirements with ease.
In conclusion, the ability to customize AWS Control Tower with Terraform empowers organizations to optimize their cloud infrastructure precisely to their specifications, paving the way for efficient hybrid cloud connectivity and agile operations.
*The code snippets provided in this blog server as a framework for understanding the deployment logic. They have been sanitized of real data and should be used for basic guidelines only.