Authorization Code Flow is a part of the OAuth 2.0 authorization protocol and it's designed to enable secure user authentication and authorization for applications to access specific resources. This flow is instrumental in protecting sensitive user data and ensuring secure access to applications.
Authorization code flow typically work with the following components:
- Auth URL: This endpoint is used to get authorization code.
- Access Token URL: This endpoint is used to exchange the authorization code for an access token.
- Client ID: Identifier that issued to client during the request process.
- Client Secret: Secret that issued to client during the request process.
- Scope: The scope of the access request. It may contains multiple values.
Let's assume we have a user pool that created basically for email accounts. We'll be covered user pool creation steps on another article.
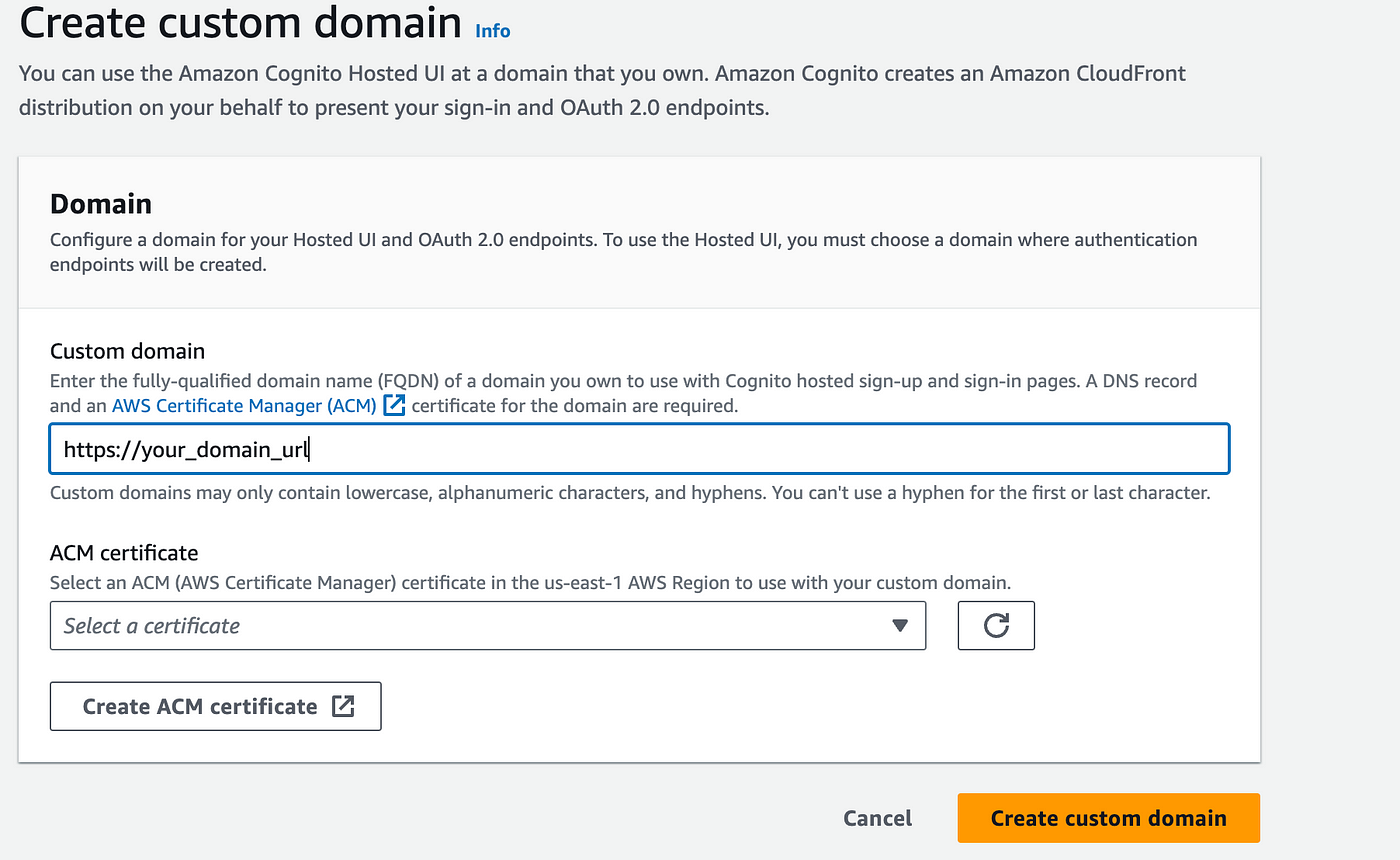
Create A Cognito Domain (Under the app integration tab)
Cognito Domain is a name where authentication endpoints will be created.
Creating A Resource Server
You can reach more information about resource server.
RFC 6749 - The OAuth 2.0 Authorization Framework (ietf.org)
We should add a custom scope that use in the resource server. I have created a scope for sample.

Creating An App Client
App clients are the user pool authentication resources attached to your app.
Let's create an app client that appropriate for authorization code flow
- Give a name for app client
- Mark generate a client secret radio button(it's optional)
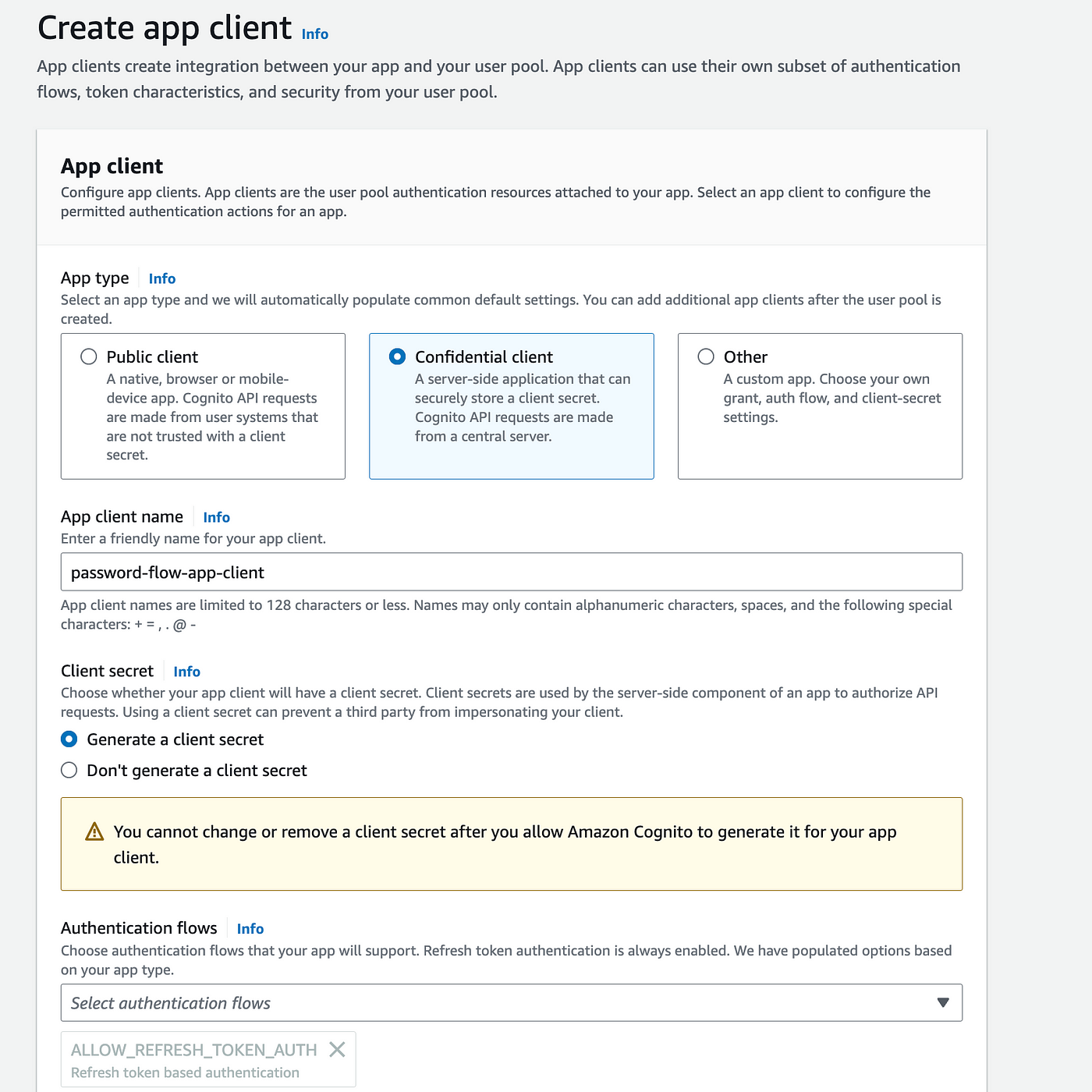
Hosted UI Settings
We are able to configure Hosted UI Settings when we create an app client
We're going to test on Postman so we need to add Postman callback URL information to Allowed callback URLs input.
https://oauth.pstmn.io/v1/callback
We should allow *authorization code grant *under the *OAuth 2.0 grant types *section.
You may choose kind of OpenID scopes under the *OpenID Connect scopes. *Also you might want to add custom scopes to access token.
Creating A Sample User
Let's create a sample user for authorization code flow.
Let's view the sample user.
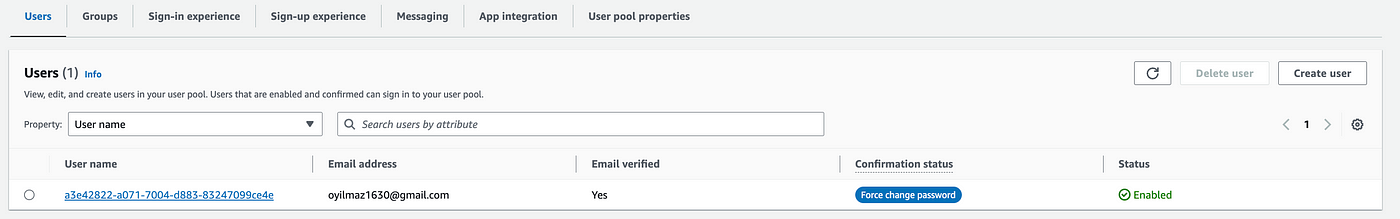
But user's confirmation status is not confirmed yet. We're going to handle user confirmation status on AWS CLI quickly.
Installing AWS CLI
You can follow the instructions for AWS CLI installation from the document below.
Install or update the latest version of the AWS CLI --- AWS Command Line Interface (amazon.com)
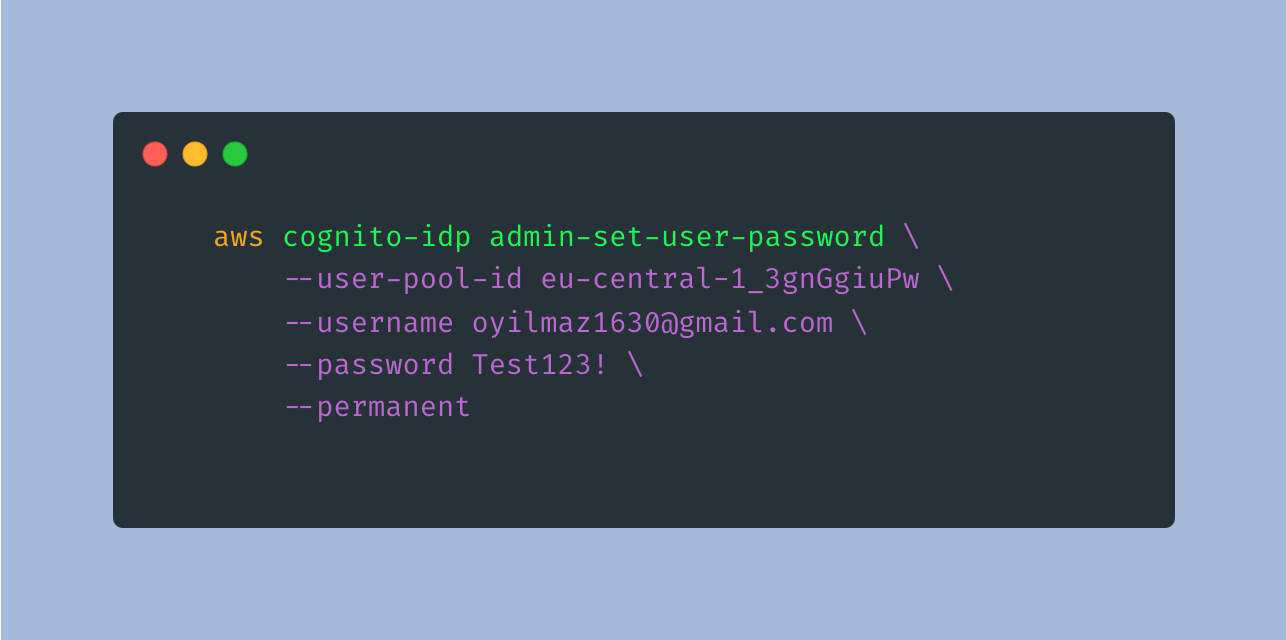
Set User Confirmation Status With AWS CLI
Let's update user status to confirmed on AWS CLI.
Let's check the user's last confirmation status
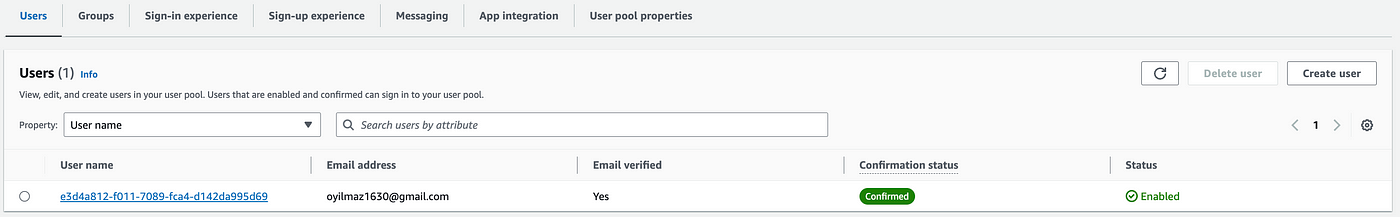
Yes. All things are set. User has been confirmed and ready to sign-in by authorization code flow.
Testing
Let's find out how to fill inputs for request on Postman.
- Go the app client page that we've created and copy Client ID and Client Secret
- Auth URL:
https://your_domain_url.auth.eu-central-1.amazoncognito.com/oauth/authorize - Access Token URL:
https://your_domain_url.auth.eu-central-1.amazoncognito.com/oauth/token
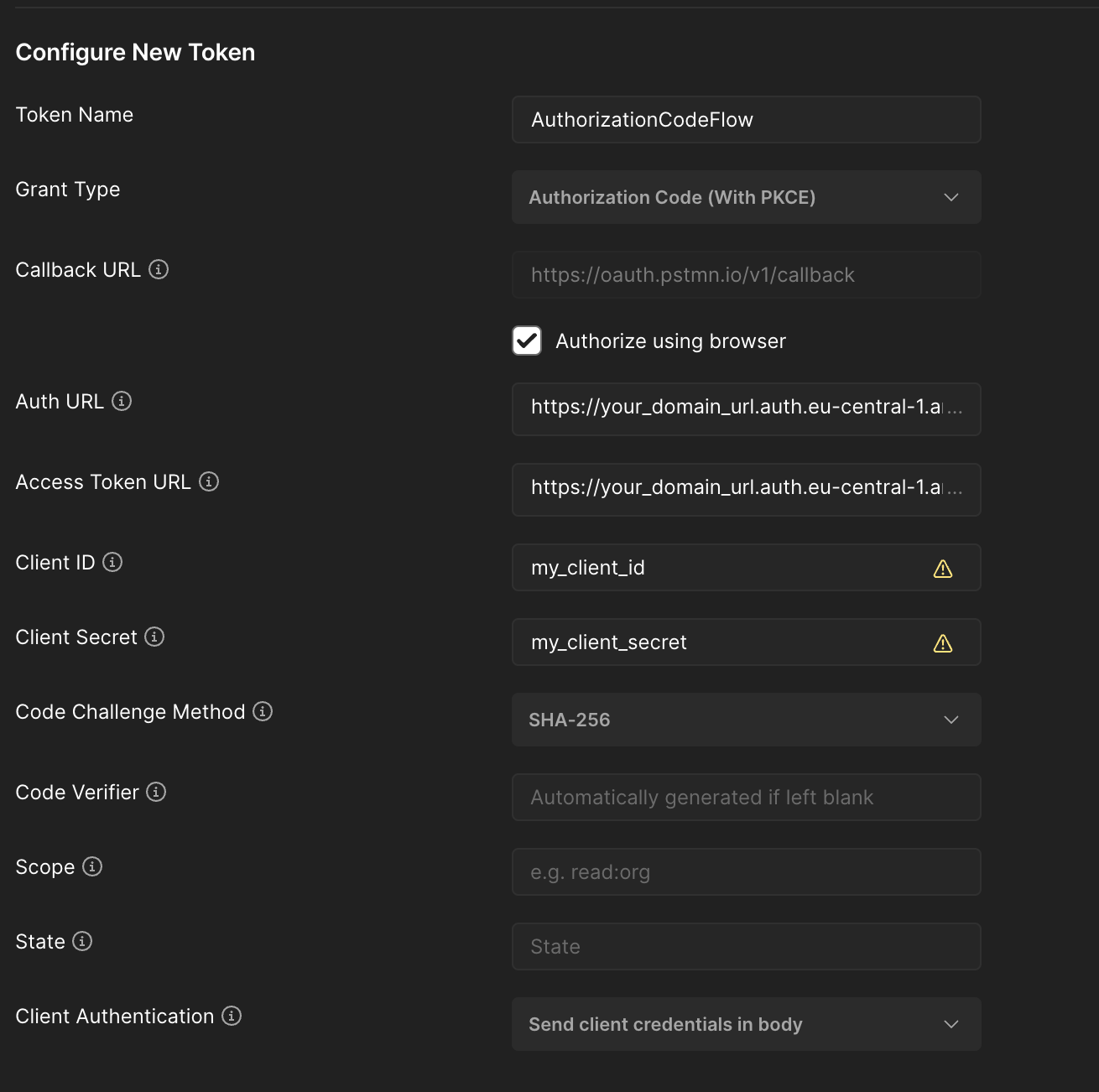
Press the Get New Access Token button and browser will open like this. This is the window that Cognito manages it. Let's fill the inputs for sign-in action.
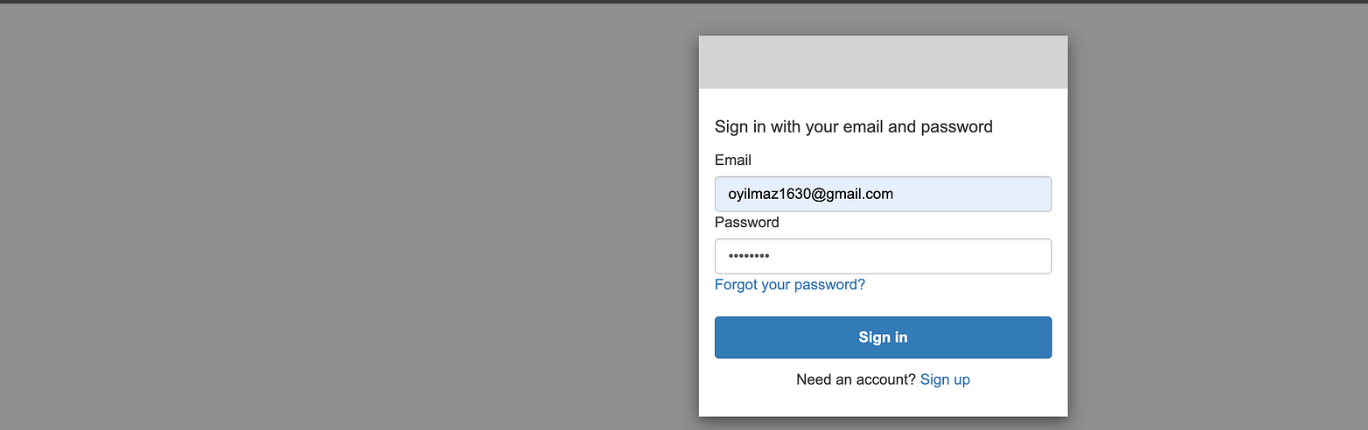
Browser has respond the result as success.
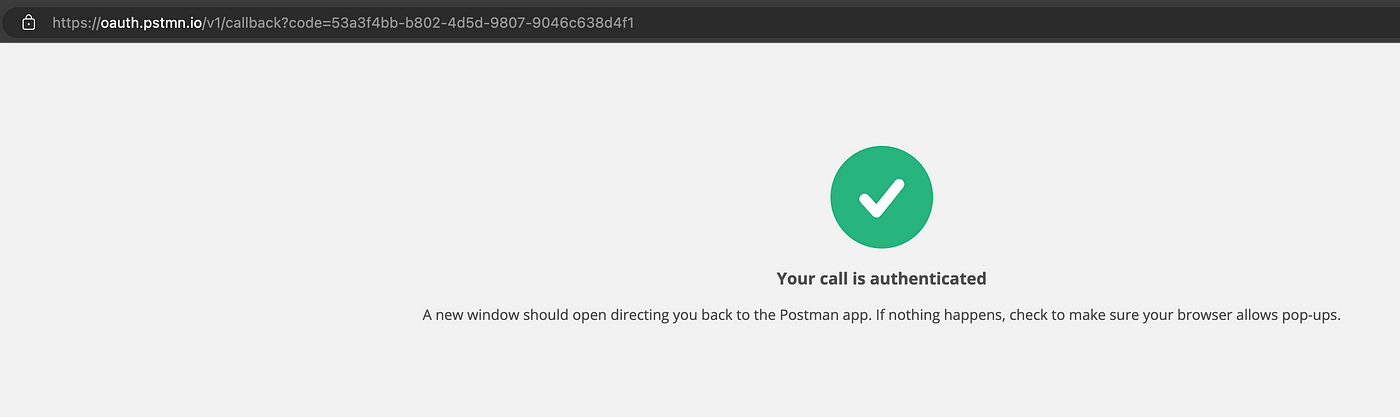
Let's check on the postman, what's going on.
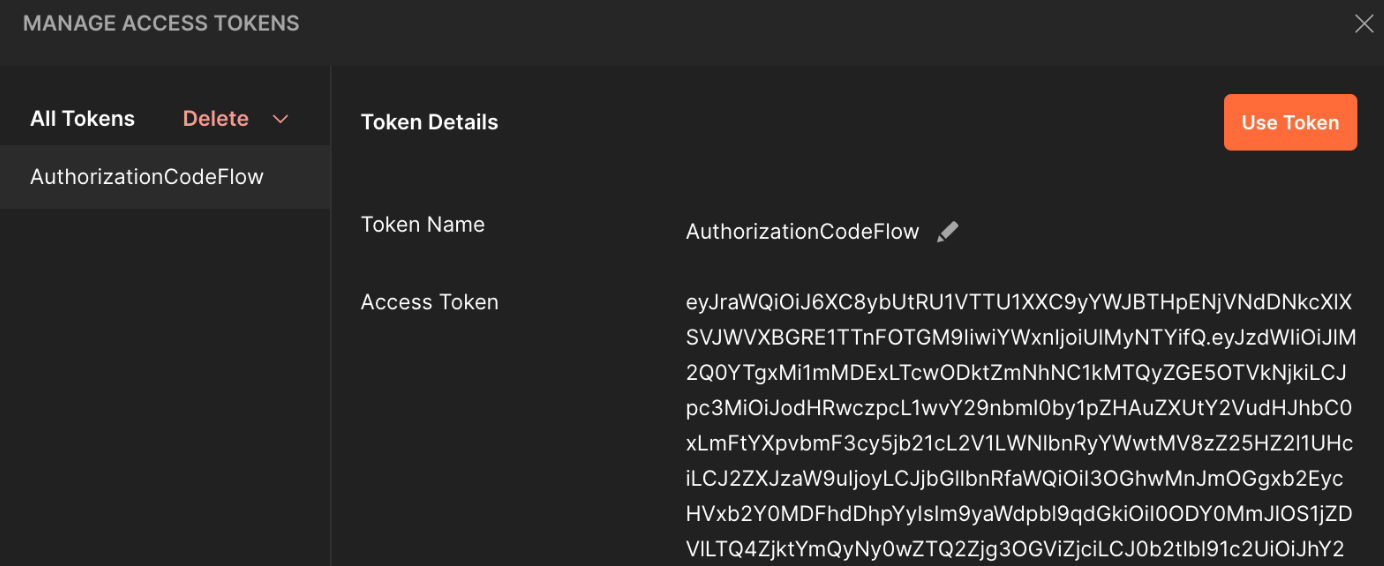
Postman received kind of tokens. These are Access, Id and Refresh tokens. Let's find out.
Access Token: eyJraWQiO.....
Token Type: Bearer
id_token: eyJraWQiOircqJPwqTyVD....
refresh_token: eyJjdHki....
access_token_url: https://your_domain_url.auth.eu-central-1.amazoncognito.com/oauth2/token
client_id: my_client_id
client_secret: my_client_secret
timestamp: 1697243273596
Finally, let's resolve the access token and view claims
{
"version": 2,
"exp": 1697246873,
"scope": "aws.cognito.signin.user.admin phone your-resource-server/order.write openid profile email",
"jti": "24a4c435-2230-428e-a9ef-0c4a3569b105",
"iss": "https://cognito-idp.eu-central-1.amazonaws.com/your_user_pool_id",
"sub": "e3d4a812-f011-7089-fca4-d142da995d69",
"origin_jti": "48642be9-cd5e-48f9-bd27-0e46f878ebf7",
"username": "f6e2b434-f011-7089-fca4-d142da995d69",
"client_id": "my_client_id",
"token_use": "access",
"auth_time": 1697243273,
"iat": 1697243273
}
Scopes are looking perfect.
Conclusion
By leveraging AWS Cognito's Authorization Code Flow, you can make your application more secure and user-friendly. This method of authentication ensures secure access to your application by validating user identities while enhancing the overall user experience. Additionally, the flexibility offered by AWS Cognito enables you to customize authentication processes to meet your specific needs.

