
What Is DevSecOps?
DevSecOps is a software development approach that merges development and operations (DevOps) with security. The goal is to ensure that DevOps teams do not compromise the security of software products to release software faster.
DevSecOps teams strive to build secure and high-quality code quickly. Instead of dealing with security only during the end of the software delivery cycle, DevSecOps integrates security practices and tools from the beginning. As a result, code is built with security into the design.
Like DevOps, DevSecOps promotes collaboration and strives to break as many silos as possible. There are no departments - there are teams working together to innovate quickly and efficiently while maintaining high standards for quality and security.
Key Elements of DevSecOps
Shifting Security to the Left
Shifting security to the left is moving work to an earlier stage in the development cycle, ensuring security standards from the onset of codebase development. When security is built in from the start, less security issues are discovered in later stages of the process, when they can cause more damage and are much more expensive to fix.
Continuous Feedback Loop
A DevSecOps team encourages all team members to improve software security with a continuous feedback loop. All teams apply fixes in bulk --- an automated process monitors software threats and provides real-time alerts to developers and security experts.
Automated Security
Automation ensures that DevSecOps standards and practices meet compliance at all the development lifecycle stages. DevSecOps teams can quickly assume more security responsibilities, like automated code analysis, compliance monitoring, incident investigation and response.
Building AWS DevSecOps CI/CD Pipeline
Building a proper DevSecOps pipeline is key to successful software production. The pipeline should include continuous integration, delivery, deployment, testing, and monitoring. Discovering vulnerabilities early in the software development life cycle (SDLC) helps reduce the impact of application changes, while accelerating software delivery. Also, transitioning DevSecOps to AWS can help optimize your operational costs and reduce the risk of DevSecOps adoption.
Security Integration
AWS offers several tools that help integrate security into the DevOps pipeline:
- AWS CodePipeline - automates detection and prevention controls to enable secure and efficient CI/CD changes.
- AWS CodeBuild - compiles and tests source code and prepares software packages for deployment.
- AWS CodeCommit - enables source control and securely hosts Git repositories. It requires configuring the Git client to support communication with the CodeCommit repositories.
- AWS CodeDeploy - automatically deploys code to on-prem, AWS-hosted, or third-party services.
- AWS CloudFormation - automatically describes and provisions infrastructure resources, enabling DevSecOps teams to create secure demo pipeline templates.
- AWS Systems Manager Parameter Store - securely stores configurations and manages secrets, providing visibility and control over the whole AWS infrastructure.
- AWS Lambda - responds to triggers by running code automatically in a serverless fashion. It supports dynamic stack validation and static code analysis.
Data Protection
Sensitive data requires protection when uploaded to a public repository or cloud service. AWS offers the following tools to help secure sensitive data:
- AWS Key Management Services - enables the creation and management of encryption keys to protect data. These services use validated hardware security modules to ensure the security of your keys.
- AWS Identity and Access Management (IAM) - tracks who made changes and helps enforce access control policies.
- Amazon Virtual Private Cloud - enables the creation of a private cloud within the public AWS cloud, offering isolation from web-based threats and other AWS customers.
Automation
A successful DevSecOps implementation relies on automation. AWS offers these security automation tools:
- AWS CloudWatch - monitors and maintains logs of AWS accounts and infrastructure components.
- AWS CloudTrail - monitors the calls to CloudWatch for AWS accounts, helping security teams to respond quickly to potential threats.
- AWS Security Hub - provides a comprehensive view of a customer's overall security posture in AWS, including a centralized pane for managing security alerts.
- Amazon Simple Notification Service (SNS) - automates communications between applications and users.
AWS DevSecOps Architecture
AWS' DevSecOps solution has the following architecture:
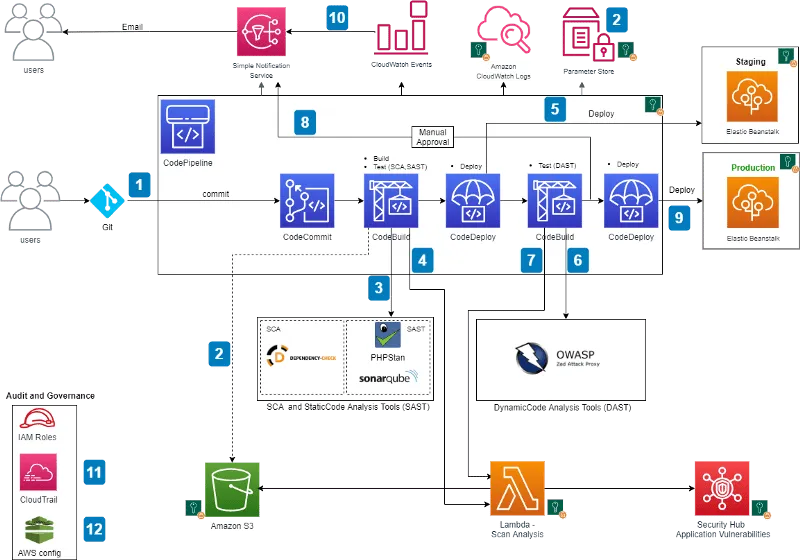
S3 bucket policies and IAM roles help secure the CI/CD pipeline and control access to resources. SSL transport and encryption help protect at-rest and in-transit pipeline data at rest. The Parameter Store can store sensitive data like passwords and API tokens, although additional measures (i.e., MFA) may be necessary to ensure regulatory compliance.
SAST, DAST, and SCA checks help implement pipeline security, although it's also possible to combine SAST and DAST into a single stage using Interactive Application Security Testing (IAST).
Here is the general workflow:
Step 1: A user commits code to the CodeCommit repository, and CloudWatch creates an event that triggers CodePipeline.
Step 2: CodeBuild packages the code, uploads the build artifacts to an S3 bucket or artifact repository (i.e., AWS CodeArtifact), retrieves authentication data from the Parameter Store, and initiates the scan.
Step 3: CodeBuild uses SCA and SAST tools to scan the code.
Step 4: If CodeBuild detects a vulnerability, it invokes a Lambda function that parses the results into the ASFF format and sends them to the Security Hub. Security Hub aggregates and displays all findings in a signal view, and the Lambda function uploads the scan results to an S3 bucket. CodeDeploy deploys the build to the Elastic Beanstalk staging environment if no vulnerabilities are detected.
Step 5: CodeBuild initiates a DAST scan (i.e., with OWASP ZAP or a BYO tool) after a successful deployment.
Step 6: If CodeBuild detects a vulnerability, it invokes a Lambda function to parse the results into ASFF and send them to the Security Hub. If no vulnerabilities are detected, it triggers the approval stage and sends an email to the approver.
Step 7: Once approved, CodeDeploy can push the code to the Elastic Beanstalk production environment.
Step 8: While the pipeline is running, CloudWatch Events records changes to the build state and notifies users via SNS messages.
Step 9: CloudTrail monitors API calls and sends alerts for critical events in the pipeline (important for auditing).
Step 10: The AWS Config service tracks all configuration changes to AWS services. It is a best security practice to add these AWS Config rules to the pipeline:
- CODEBUILD_PROJECT_ENVVAR_AWSCRED_CHECK - verifies that the project contains access key environment variables. If the variables contain credentials in plain text, the rule is non-compliant.
- CLOUD_TRAIL_LOG_FILE_VALIDATION_ENABLED - verifies that CloudTrail generates signed digest files with logs. It is important to enable file validation on all cloud trails; otherwise, the rule is non-compliant.
Conclusion
In this article, I explained the basics of DevSecOps and showed how to create a secure development pipeline using AWS services. AWS can support DevSecOps across the software development lifecycle:
- Security integration - scanning and detecting security issues in the build, CI, and deployment process using tools like AWS CodePipeline and CodeDeploy.
- Data protection - securing sensitive data via Amazon's robust Identity and Access Management (IAM) and Key Management Service (KMS).
- Automation - providing data to fuel automated security processes, in particular monitoring and log data from CloudWatch and CloudTrail.
I hope this will be useful as you build your cloud-based DevSecOps development process.
Comments
Loading comments…