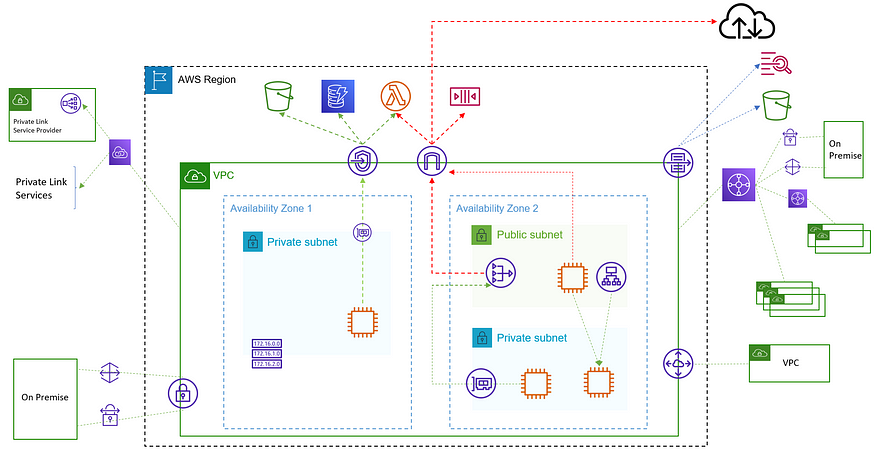
The above diagram depicts the major components of the AWS VPC service. Let us go through them one by one.
VPC
Virtual Private Cloud is a service from AWS which enables us to launch AWS resources in a logically isolated virtual network (similar to a local data center). It gives us complete control over our virtual networking environment, including resource placement (which AZ), connectivity(route table, peering), and security (Security Group & NACL). It is a regional service. By default, each region in our account will have a default VPC for us to quickly start.
CIDR
To create a VPC we need to supply a Classless Inter-Domain Routing (CIDR) block. Our VPC must be /16 or smaller. We need to be careful in selecting the right size of VPC as we can not modify the range of an existing CIDR block.

An IPv4 address is represented as four 8-bit decimal numbers or octets separated by dots. Prefix number (Mask) is the number of bits locked from the left side. In the above example, the first 16 bits are fixed. The remaining (32 -16=16) bits’ permutations will decide the IPs in the subnet.
Internet Gateway
The next thing we need once we have VPC is the ability to access the resources from local over the internet. Internet Gateway is the component that allows resources in the VPC to reach & be reachable over the internet. We create an IGW, then attach it to a VPC and add a route to the routing table (explanation later) pointing to IGW Id. IGW will do a 1-to-1 NAT for the instance address.
To internet: Response address is changed from private IP to instance's public/elastic IP.
From the internet: Target public IP is changed to private IP address of the instance.
Subnet
A subnet is a range (subset) of IP addresses in your VPC. Each subnet is tied to one AZ.
Public Subnet: If a subnet is associated with a route table that has a route to an internet gateway, it’s known as a public subnet.
Private Subnet: If a subnet is associated with a route table that does not have a route to an internet gateway, it’s known as a private subnet.
Route table
Every resource created in a subnet gets a private IP address from the CIDR of the subnet. And instances communicate with each other using this IP. How to reach a particular IP is defined in the subnets associated route table. The table has the following structure. A destination and the target for the destination.

If our route table has multiple routes, the most specific route that matches the traffic (longest prefix match) will be applied. Let us say we want to reach 10.1.1.24 and in the route table, we have two routes, one for 10.1.1.0/24 and the other 10.1.0.0/16, then it will use the first one.
Elastic Network Interface
An elastic network interface is a logical networking component in a VPC that represents a virtual network card. Security groups are tied to these interfaces. We can attach multiple interfaces to an instance. Also, each ENI can have multiple private IPs. In EKS we use multiple ENIs and multiple IPs to launch multiple pods on the same EC2 with different IPs.
Another use case is a Dual homed EC2.

Elastic IP Address
An Elastic IP is a static public IP address that we can attach to our AWS Account. These IPs are fixed, unlike public IPs which change on instance termination. We can allocate an IP from AWS managed IP or bring our own IP to AWS.
Security Group
A security group acts as a firewall to control inbound and outbound traffic on the ENI. Security groups are stateful. This means when in initiate a request the response traffic for that request is allowed to flow in regardless of inbound security group rules & vice versa. By default, it allows all outbound traffic and denies all inbound traffic.

Network Access Control List
NACLs act as a firewall at the subnet level. A custom NACL by default denies all inbound and outbound traffic. Network ACLs are stateless, which means that responses to allowed inbound traffic are subject to the rules for outbound traffic (and vice versa). Each subnet can only be attached to one NACL.
NAT Gateway
We saw that resources in the private subnet cant be reached from the internet and they also cant reach the internet. But we need access to the internet for various use cases like downloading software. To enable the host from the private subnet to reach the internet we use NAT. NAT device enables instances in a private subnet to connect to the internet but prevents hosts on the internet from initiating connections with the instances. NAT does the Address translation from private IP to its own public IP. Must be created in a public subnet for accessing internet addresses.
5–45 Gbps Bandwidth
55,000 connections per minute for destination IP & port combination
VPC Endpoint
To access AWS services that are not in a VPC like S3, DynamoDb, SNS, and SQS we need to traverse the internet. To reduce the traffic & security AWS provides a service called VPC Endpoint. VPC endpoints are virtual devices. What it does is, creates a prefix-list route in the private subnet’s route table. The endpoint gets a private IP from the selected subnet. Since the IPs are private we don't need to use NAT or IGW. This way the traffic never leaves the AWS network. These endpoints are local to the region and scoped to one VPC. It also supports endpoint policies, using this we can control what can go through these endpoints.

Prefix List
A Managed Prefix List is a collection of CIDR blocks created from addresses we frequently use. We can use prefix lists to make it easier to configure and maintain our security groups and route tables.
Customer Managed Prefix List
AWS Managed Prefix List

Private Link
AWS PrivateLink is a highly available, scalable technology that enables you to privately connect your VPC to supported AWS services, services hosted by other AWS accounts (VPC endpoint services), and supported AWS Marketplace partner services. It requires an NLB and can be configured from the NLB page.


DHCP Options
The Dynamic Host Configuration Protocol (DHCP) is a standard way of passing configuration information hosts on a TCP/IP network. We can create our own DHCP options for our VPC. We can change the following configuration according to our needs:
DNS Name
DNS Servers
NTP Servers
Settings that can be configured:
enableDnsSupport — Amazon-provided DNS server at 169.254.169.253
enableDnsHostname — Instances VPC will get public DNS hostnames
VPC Peering
A VPC peering connection allows two non-overlapping VPCs to behave as if they are one network. Instances in either VPC can communicate with each other using their private address. Peering connection is created using was infrastructure itself. VPC peering needs to be done in a full mesh way as it does not support edge routing and transitive peering. For an account with N VPCs, we will need (N*(N-1))/2 peering connections will be needed. On top of this, each VPC can have a max of 125 peering connections.
Transit Gateway
AWS Transit Gateway acts as a cloud router & simplifies network architecture by removing the need to have complex point-to-point VPC peering. Traffic between VPC and Transit Gateway remains on the AWS private network. Transit Gateway operates on Layer 3. A transit gateway has three major components — 1. Attachment 2. Association 3. Propagation

Unlike Private Link, TGW bothers about overlapping CIDRs. If we have a requirement of unidirectional traffic from one VPC to other VPC we can leverage Private Link, Route53 Resolver to achieve a cost-efficient solution.
Route53 + Transit Gateway
PrivateLink + Route 53 Resolver
VPN
AWS VPN establishes secure connections between on-premises networks, remote offices, client devices, and the AWS VPC. We can extend our on-premises networks to the cloud and securely access them from anywhere. On the AWS side of the VPN connection, a Virtual Private Gateway is created. This creates two VPN tunnels (with the public IP addresses). On the on-premise side, a customer gateway (just a representation of the customer’s router) is provisioned. In the end, the route table is updated to use the “vgw” as the target for the on-premise IPs.

Direct Connect
Direct Connect establishes private connectivity between AWS and our data center, office, or collocated environment. Direct Connect combination of virtual private gateways & private virtual interfaces. Each VIF is a single VLAN connection between AWS and our Service provider network. We can also provision Public VIF so that services like S3, DynamoDbs can be accessed over a secure & fast network from our data centers.

VPC Flow Log
VPC Flow adds the observability aspect to VPC. This feature enables us to capture information about the IP traffic going to and from network interfaces in our VPC. Aggregation is done at 1 min intervals. So it is not real-time. Since the log is collected outside of the network traffic path, so there is no added latency.

Traffic Mirroring
Traffic Mirroring is a feature that we can use to copy network traffic from an ENI of EC2 instances. The copied traffic can then be filtered and forwarded to out-of-band security and monitoring appliances for content inspection, threat monitoring & troubleshooting, etc.

Reachability Analyzer
This is a tool to test connectivity between a source and destination in our VPC. It lists hop-by-hop details of the network path between the source and the destination. In case of failures, it identifies the blocking component.

Bonus.
Shared VPC design
A shared VPC design allows us to have one VPC shared across multiple accounts. This can be useful in centralizing networking work in one account. In the below image we have a VPC shared with three accounts. The public subnet is in the owner account and only private subnets are shared. Any modification to the endpoint, NAT, IGW, or NACL will apply to all accounts which are sharing those subnets.

In this blog, we went through the basics of VPC in AWS. There are other aspects like DHCP, DNS resolution, Route propagation, Network Appliances. Those we will discuss in another blog.